category
重要事项
本文中描述的一些功能可能仅在预览版中可用。此预览版没有服务级别协议,我们不建议将其用于生产工作负载。某些功能可能不受支持或功能受限。有关详细信息,请参阅Microsoft Azure预览版的补充使用条款。
在本文中,您将学习如何管理对Azure AI Studio中心的访问(授权)。Azure基于角色的访问控制(Azure RBAC)用于管理对Azure资源的访问,例如创建新资源或使用现有资源的能力。您的Microsoft Entra ID中的用户被分配了特定的角色,这些角色授予对资源的访问权限。Azure提供内置角色和创建自定义角色的能力。
警告
应用某些角色可能会限制其他用户在Azure AI Studio中的UI功能。例如,如果用户的角色没有创建计算实例的能力,那么在studio中创建计算实例选项将不可用。这种行为是预期的,可以防止用户尝试返回拒绝访问错误的操作。
AI工作室中心vs项目
在Azure AI Studio中,有两个访问级别:中心和项目。该中心是基础设施(包括虚拟网络设置、客户管理的密钥、管理的身份和策略)的所在地,也是配置Azure AI服务的地方。集线器访问允许您修改基础架构、创建新集线器和创建项目。项目是中心的一个子集,充当工作区,允许您构建和部署AI系统。在项目中,您可以开发流程、部署模型和管理项目资产。项目访问允许您在利用集线器上的基础设施设置的同时,端到端地开发AI。
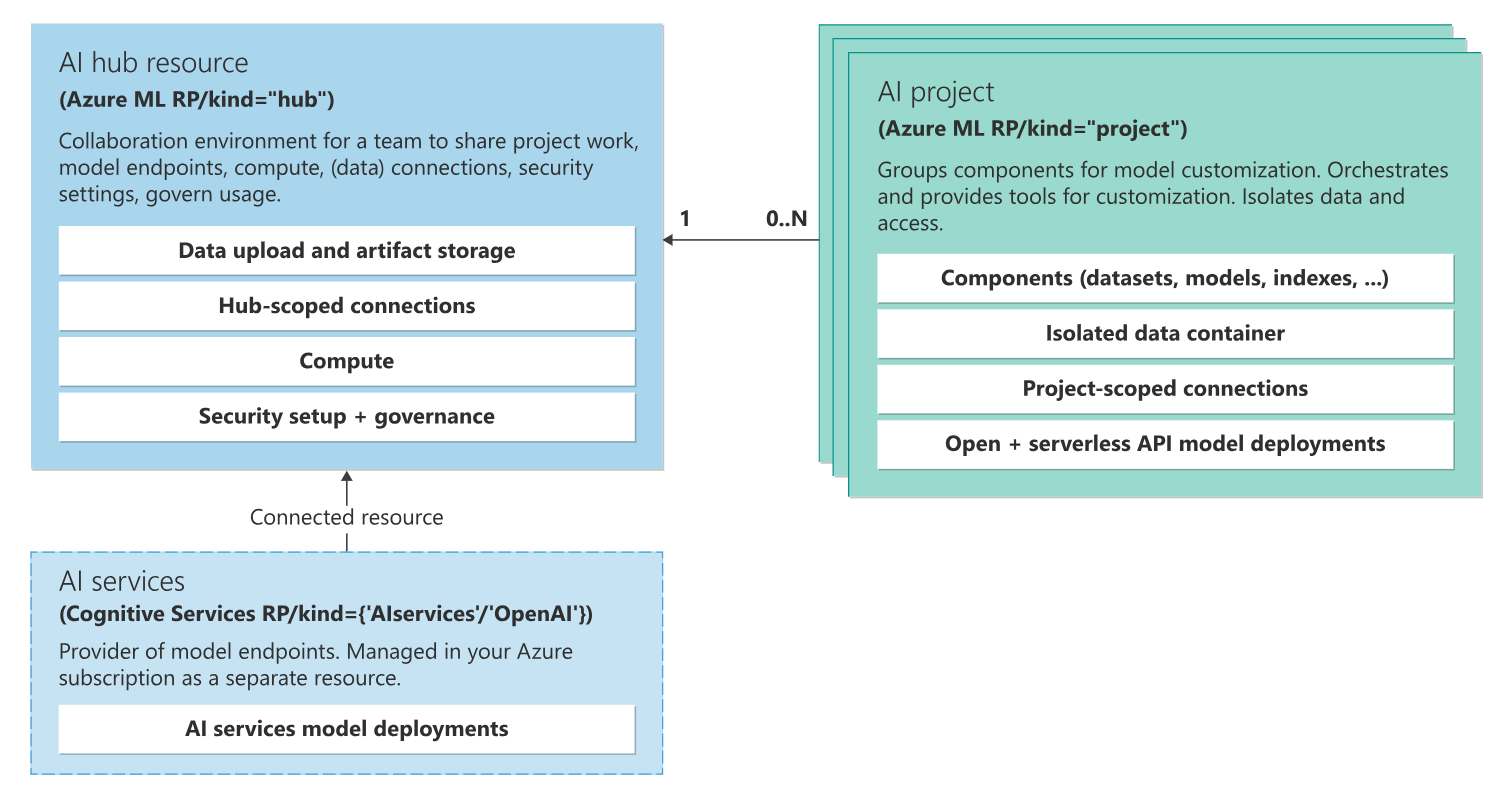
AI Studio资源之间的关系图。
中心和项目关系的一个关键好处是,开发人员可以创建自己的项目,继承中心安全设置。您也可能有开发人员是项目的贡献者,无法创建新项目。
中心的默认角色
AI Studio中心具有默认可用的内置角色。
以下是集线器的内置角色及其权限表:
| Role | Description |
|---|---|
| Owner | Full access to the hub, including the ability to manage and create new hubs and assign permissions. This role is automatically assigned to the hub creator |
| Contributor | User has full access to the hub, including the ability to create new hubs, but isn't able to manage hub permissions on the existing resource. |
| Azure AI Developer | Perform all actions except create new hubs and manage the hub permissions. For example, users can create projects, compute, and connections. Users can assign permissions within their project. Users can interact with existing Azure AI resources such as Azure OpenAI, Azure AI Search, and Azure AI services. |
| Azure AI Inference Deployment Operator | Perform all actions required to create a resource deployment within a resource group. |
| Reader | Read only access to the hub. This role is automatically assigned to all project members within the hub. |
Contributor和Azure AI Developer之间的关键区别在于创建新中心的能力。如果您不希望用户创建新的中心(由于配额、成本或只是管理您拥有的中心数量),请分配Azure AI开发人员角色。
只有所有者和贡献者角色允许您创建中心。此时,自定义角色无法授予您创建中心的权限。
新的“Azure AI开发人员”角色的全套权限如下:
JSON
{
"Permissions": [
{
"Actions": [
"Microsoft.MachineLearningServices/workspaces/*/read",
"Microsoft.MachineLearningServices/workspaces/*/action",
"Microsoft.MachineLearningServices/workspaces/*/delete",
"Microsoft.MachineLearningServices/workspaces/*/write"
],
"NotActions": [
"Microsoft.MachineLearningServices/workspaces/delete",
"Microsoft.MachineLearningServices/workspaces/write",
"Microsoft.MachineLearningServices/workspaces/listKeys/action",
"Microsoft.MachineLearningServices/workspaces/hubs/write",
"Microsoft.MachineLearningServices/workspaces/hubs/delete",
"Microsoft.MachineLearningServices/workspaces/featurestores/write",
"Microsoft.MachineLearningServices/workspaces/featurestores/delete"
],
"DataActions": [
"Microsoft.CognitiveServices/accounts/OpenAI/*",
"Microsoft.CognitiveServices/accounts/SpeechServices/*",
"Microsoft.CognitiveServices/accounts/ContentSafety/*"
],
"NotDataActions": [],
"Condition": null,
"ConditionVersion": null
}
]
}
项目的默认角色
AI Studio中的项目具有默认可用的内置角色。
以下是项目的内置角色及其权限表:
| Role | Description |
|---|---|
| Owner | Full access to the project, including the ability to assign permissions to project users. |
| Contributor | User has full access to the project but can't assign permissions to project users. |
| Azure AI Developer | User can perform most actions, including create deployments, but can't assign permissions to project users. |
| Azure AI Inference Deployment Operator | Perform all actions required to create a resource deployment within a resource group. |
| Reader | Read only access to the project. |
当用户被授予访问项目的权限时(例如,通过AI Studio权限管理),会自动为该用户分配另外两个角色。第一个角色是中心的读者。第二个角色是推理部署操作员角色,它允许用户在项目所在的资源组上创建部署。此角色由以下两个权限组成:“Microsoft.Authorization/*/read”和“Microsoft.Resources/deplorations/*”。
为了完成端到端的AI开发和部署,用户只需要这两个自动分配的角色,以及项目上的参与者或Azure AI开发人员角色。
创建项目所需的最小权限是具有Microsoft允许操作的角色。机器学习服务/工作区/中心/在中心加入。Azure AI Developer内置角色具有此权限。
依赖服务Azure RBAC权限
该中心依赖于其他Azure服务。下表列出了创建集线器时这些服务所需的权限。创建中心的人需要这些权限。从中心创建项目的人不需要它们。
| Permission | Purpose |
|---|---|
Microsoft.Storage/storageAccounts/write |
Create a storage account with the specified parameters or update the properties or tags or adds custom domain for the specified storage account. |
Microsoft.KeyVault/vaults/write |
Create a new key vault or updates the properties of an existing key vault. Certain properties might require more permissions. |
Microsoft.CognitiveServices/accounts/write |
Write API Accounts. |
Microsoft.MachineLearningServices/workspaces/write |
Create a new workspace or updates the properties of an existing workspace. |
企业RBAC设置示例
下表是如何为企业的Azure AI Studio设置基于角色的访问控制的示例。
| Persona | Role | Purpose |
|---|---|---|
| IT admin | Owner of the hub | The IT admin can ensure the hub is set up to their enterprise standards. They can assign managers the Contributor role on the resource if they want to enable managers to make new hubs. Or they can assign managers the Azure AI Developer role on the resource to not allow for new hub creation. |
| Managers | Contributor or Azure AI Developer on the hub | Managers can manage the hub, audit compute resources, audit connections, and create shared connections. |
| Team lead/Lead developer | Azure AI Developer on the hub | Lead developers can create projects for their team and create shared resources (such as compute and connections) at the hub level. After project creation, project owners can invite other members. |
| Team members/developers | Contributor or Azure AI Developer on the project | Developers can build and deploy AI models within a project and create assets that enable development such as computes and connections. |
访问在中心之外创建的资源
创建中心时,内置的基于角色的访问控制权限授予您使用资源的权限。但是,如果您希望使用代表您创建的资源之外的资源,则需要确保:
- 您尝试使用的资源已设置权限,允许您访问它。
- 允许您的集线器访问它。
例如,如果您试图使用新的Blob存储,则需要确保将集线器的托管标识添加到Blob的Blob存储读取器角色中。如果您正尝试使用新的Azure AI搜索源,则可能需要将中心添加到Azure AI搜索的角色分配中。
使用角色管理访问权限
如果你是一个中心的所有者,你可以添加和删除AI Studio的角色。转到AI Studio的主页并选择您的中心。然后选择“用户”以添加和删除中心的用户。您还可以在访问控制(IAM)下从Azure门户或通过Azure CLI管理权限。例如,使用Azure CLI将Azure AI开发人员角色分配给“joe@contoso.com对于资源组“this rg”,使用以下命令:
Azure命令行界面
az role assignment create --role "Azure AI Developer" --assignee "joe@contoso.com" --resource-group this-rg
创建自定义角色
注:为了创建一个新的中心,您需要所有者或贡献者角色。此时,即使允许所有操作,自定义角色也无法使您创建中心。
如果内置角色不足,您可以创建自定义角色。自定义角色可能在该AI Studio中具有读取、写入、删除和计算资源权限。您可以使角色在特定项目级别、特定资源组级别或特定订阅级别可用。
注:
您必须是该级别资源的所有者,才能在该资源中创建自定义角色。
以下JSON示例定义了订阅级别的自定义AI Studio开发人员角色:
{
"properties": {
"roleName": "AI Studio Developer",
"description": "Custom role for AI Studio. At subscription level",
"assignableScopes": [
"/subscriptions/<your-subscription-id>"
],
"permissions": [
{
"actions": [
"Microsoft.MachineLearningServices/workspaces/write",
"Microsoft.MachineLearningServices/workspaces/endpoints/write",
"Microsoft.Storage/storageAccounts/write",
"Microsoft.Resources/deployments/validate/action",
"Microsoft.KeyVault/vaults/write",
"Microsoft.Authorization/roleAssignments/read",
"Microsoft.Authorization/roleDefinitions/read",
"Microsoft.CognitiveServices/*/read"
],
"notActions": [
"Microsoft.MachineLearningServices/workspaces/delete",
"Microsoft.MachineLearningServices/workspaces/write",
"Microsoft.MachineLearningServices/workspaces/listKeys/action",
"Microsoft.MachineLearningServices/workspaces/hubs/write",
"Microsoft.MachineLearningServices/workspaces/hubs/delete",
"Microsoft.MachineLearningServices/workspaces/featurestores/write",
"Microsoft.MachineLearningServices/workspaces/featurestores/delete"
],
"dataActions": [
"Microsoft.CognitiveServices/accounts/OpenAI/*/read",
"Microsoft.CognitiveServices/accounts/OpenAI/engines/completions/action",
"Microsoft.CognitiveServices/accounts/OpenAI/engines/search/action",
"Microsoft.CognitiveServices/accounts/OpenAI/engines/generate/action",
"Microsoft.CognitiveServices/accounts/OpenAI/deployments/search/action",
"Microsoft.CognitiveServices/accounts/OpenAI/deployments/completions/action",
"Microsoft.CognitiveServices/accounts/OpenAI/deployments/chat/completions/action",
"Microsoft.CognitiveServices/accounts/OpenAI/deployments/extensions/chat/completions/action",
"Microsoft.CognitiveServices/accounts/OpenAI/deployments/embeddings/action",
"Microsoft.CognitiveServices/accounts/OpenAI/images/generations/action"
],
"notDataActions": []
}
]
}
}场景:使用客户管理的密钥
当配置集线器以使用客户管理密钥(CMK)时,Azure密钥库用于存储密钥。用于创建工作区的用户或服务主体必须具有密钥库的所有者或贡献者访问权限。
如果您的AI Studio中心配置了用户分配的托管身份,则必须授予该身份以下角色。这些角色允许托管身份创建使用客户托管密钥时使用的Azure存储、Azure Cosmos DB和Azure搜索资源:
Microsoft.Storage/storageAccounts/writeMicrosoft.Search/searchServices/writeMicrosoft.DocumentDB/databaseAccounts/write
在密钥库中,用户或服务主体必须通过密钥库访问策略具有对密钥的创建、获取、删除和清除访问权限。有关详细信息,请参阅Azure密钥库安全。
场景:使用现有的Azure OpenAI资源
当您创建与现有Azure OpenAI资源的连接时,您还必须为用户分配角色,以便他们可以访问该资源。您应该根据需要执行的任务分配认知服务OpenAI用户或认知服务OpenAIContributor角色。有关这些角色及其启用的任务的信息,请参阅Azure OpenAI角色。
场景:使用Azure容器注册表
Azure容器注册表实例是Azure AI Studio中心的可选依赖项。下表列出了向Azure容器注册表验证集线器时的支持矩阵,具体取决于身份验证方法和Azure容器注册表的公共网络访问配置。
| Authentication method | Public network access disabled |
Azure Container Registry Public network access enabled |
|---|---|---|
| Admin user | ✓ | ✓ |
| AI Studio hub system-assigned managed identity | ✓ | ✓ |
| AI Studio hub user-assigned managed identity with the ACRPull role assigned to the identity |
✓ |
创建集线器时,系统分配的托管标识会自动分配给正确的角色。如果您使用的是用户分配的托管身份,则必须将ACRPull角色分配给该身份。
场景:使用Azure应用程序洞察进行日志记录
Azure Application Insights是Azure AI Studio中心的可选依赖项。下表列出了在创建中心时使用Application Insights所需的权限。创建中心的人需要这些权限。从中心创建项目的人不需要这些权限。
| Permission | Purpose |
|---|---|
Microsoft.Insights/Components/Write |
Write to an application insights component configuration. |
Microsoft.OperationalInsights/workspaces/write |
Create a new workspace or links to an existing workspace by providing the customer ID from the existing workspace. |
场景:供应吞吐量单位采购商
以下示例定义了一个可以获取配置吞吐量单元(PTU)的自定义角色。
{
"properties": {
"roleName": "PTU procurer",
"description": "Custom role to purchase PTU",
"assignableScopes": [
"/subscriptions/<your-subscription-id>"
],
"permissions": [
{
"actions": [
"Microsoft.CognitiveServices/accounts/commitmentplans/read",
"Microsoft.CognitiveServices/accounts/commitmentplans/write",
"Microsoft.CognitiveServices/accounts/commitmentplans/delete",
"Microsoft.CognitiveServices/locations/commitmentTiers/read",
"Microsoft.CognitiveServices/accounts/commitmentplans/read",
"Microsoft.CognitiveServices/accounts/commitmentplans/write",
"Microsoft.CognitiveServices/accounts/commitmentplans/delete",
"Microsoft.Features/features/read",
"Microsoft.Features/providers/features/read",
"Microsoft.Features/providers/features/register/action",
"Microsoft.Insights/logDefinitions/read",
"Microsoft.Insights/metricdefinitions/read",
"Microsoft.Insights/metrics/read",
"Microsoft.ResourceHealth/availabilityStatuses/read",
"Microsoft.Resources/deployments/operations/read",
"Microsoft.Resources/subscriptions/operationresults/read",
"Microsoft.Resources/subscriptions/read",
"Microsoft.Resources/subscriptions/resourcegroups/deployments/*",
"Microsoft.Resources/subscriptions/resourceGroups/read"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}场景:Azure OpenAI助手API
以下示例为使用Azure OpenAI Assistant的开发人员定义了一个角色。
{
"id": "",
"properties": {
"roleName": "CognitiveServices OpenAI Assistants API Developer",
"description": "Custom role to work with AOAI Assistants API",
"assignableScopes": [
"<your-scope>"
],
"permissions": [
{
"actions": [
"Microsoft.CognitiveServices/*/read",
"Microsoft.Authorization/roleAssignments/read",
"Microsoft.Authorization/roleDefinitions/read"
],
"notActions": [],
"dataActions": [
"Microsoft.CognitiveServices/accounts/OpenAI/*/read",
"Microsoft.CognitiveServices/accounts/OpenAI/engines/completions/action",
"Microsoft.CognitiveServices/accounts/OpenAI/engines/search/action",
"Microsoft.CognitiveServices/accounts/OpenAI/engines/generate/action",
"Microsoft.CognitiveServices/accounts/OpenAI/deployments/search/action",
"Microsoft.CognitiveServices/accounts/OpenAI/deployments/completions/action",
"Microsoft.CognitiveServices/accounts/OpenAI/deployments/chat/completions/action",
"Microsoft.CognitiveServices/accounts/OpenAI/deployments/extensions/chat/completions/action",
"Microsoft.CognitiveServices/accounts/OpenAI/deployments/embeddings/action",
"Microsoft.CognitiveServices/accounts/OpenAI/images/generations/action",
"Microsoft.CognitiveServices/accounts/OpenAI/assistants/write",
"Microsoft.CognitiveServices/accounts/OpenAI/assistants/read",
"Microsoft.CognitiveServices/accounts/OpenAI/assistants/delete",
"Microsoft.CognitiveServices/accounts/OpenAI/assistants/files/write",
"Microsoft.CognitiveServices/accounts/OpenAI/assistants/files/read",
"Microsoft.CognitiveServices/accounts/OpenAI/assistants/files/delete",
"Microsoft.CognitiveServices/accounts/OpenAI/assistants/threads/write",
"Microsoft.CognitiveServices/accounts/OpenAI/assistants/threads/read",
"Microsoft.CognitiveServices/accounts/OpenAI/assistants/threads/delete",
"Microsoft.CognitiveServices/accounts/OpenAI/assistants/threads/messages/write",
"Microsoft.CognitiveServices/accounts/OpenAI/assistants/threads/messages/read",
"Microsoft.CognitiveServices/accounts/OpenAI/assistants/threads/messages/files/read",
"Microsoft.CognitiveServices/accounts/OpenAI/assistants/threads/runs/write",
"Microsoft.CognitiveServices/accounts/OpenAI/assistants/threads/runs/read",
"Microsoft.CognitiveServices/accounts/OpenAI/assistants/threads/runs/steps/read"
],
"notDataActions": []
}
]
}
}下一步行动
- 登录 发表评论
- 11 次浏览
Tags
最新内容
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago