Chinese, Simplified
category
由于您的组织可能已经具备零信任保护的要素,因此本文档集提供了概念信息,以帮助您开始使用,并提供了端到端遵守零信任原则的部署计划和实施建议。每篇文章都是部署目标的清单,包括步骤和更多信息的链接。
通过在七个技术支柱中实施零信任控制和技术,您可以在整个IT基础设施中部署零信任原则。其中六个支柱是信号源、执法控制平面和需要防御的关键资源。在这些方面,有一个支柱负责收集这些信号,为安全事件提供可见性,并为应对和减轻网络安全威胁提供自动化和编排。
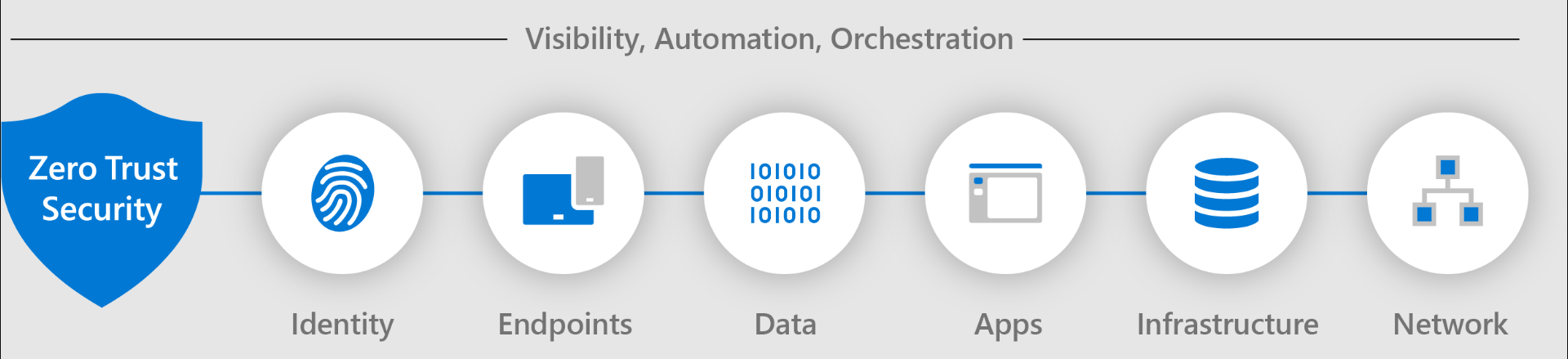
Zero Trust中可见性、自动化和编排元素的示意图。
以下文章提供了这七个技术支柱的概念信息和部署目标。使用这些文章来评估您的准备情况,并制定应用零信任原则的部署计划。
Recommended training
| Training | Establish the guiding principles and core components of Zero Trust |
|---|---|
 |
Use this learning path to understand the basics of applying Zero Trust principles to the key technology pillars of identities, endpoints, application access, networks, infrastructure, and data. |
Additional Zero Trust resources
Use these additional Zero Trust resources based on a documentation set or roles in your organization.
Documentation set
Follow this table for the best Zero Trust documentation sets for your needs.
| Documentation set | Helps you... | Roles |
|---|---|---|
| Adoption framework for phase and step guidance for key business solutions and outcomes | Apply Zero Trust protections from the C-suite to the IT implementation. | Security architects, IT teams, and project managers |
| Zero Trust for small businesses | Apply Zero Trust principles to small business customers. | Customers and partners working with Microsoft 365 for business |
| Zero Trust Rapid Modernization Plan (RaMP) for project management guidance and checklists for easy wins | Quickly implement key layers of Zero Trust protection. | Security architects and IT implementers |
| Zero Trust deployment plan with Microsoft 365 for stepped and detailed design and deployment guidance | Apply Zero Trust protections to your Microsoft 365 tenant. | IT teams and security staff |
| Zero Trust for Microsoft Copilots for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Microsoft Copilots. | IT teams and security staff |
| Zero Trust for Azure services for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Azure workloads and services. | IT teams and security staff |
| Partner integration with Zero Trust for design guidance for technology areas and specializations | Apply Zero Trust protections to partner Microsoft cloud solutions. | Partner developers, IT teams, and security staff |
| Develop using Zero Trust principles for application development design guidance and best practices | Apply Zero Trust protections to your application. | Application developers |
Your role
Follow this table for the best documentation sets for the roles in your organization.
| Role | Documentation set | Helps you... |
|---|---|---|
| Security architect IT project manager IT implementer |
Adoption framework for phase and step guidance for key business solutions and outcomes | Apply Zero Trust protections from the C-suite to the IT implementation. |
| Customer or partner for Microsoft 365 for business | Zero Trust for small businesses | Apply Zero Trust principles to small business customers. |
| Security architect IT implementer |
Zero Trust Rapid Modernization Plan (RaMP) for project management guidance and checklists for easy wins | Quickly implement key layers of Zero Trust protection. |
| Member of an IT or security team for Microsoft 365 | Zero Trust deployment plan with Microsoft 365 for stepped and detailed design and deployment guidance for Microsoft 365 | Apply Zero Trust protections to your Microsoft 365 tenant. |
| Member of an IT or security team for Microsoft Copilots | Zero Trust for Microsoft Copilots for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Microsoft Copilots. |
| Member of an IT or security team for Azure services | Zero Trust for Azure services for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Azure workloads and services. |
| Partner developer or member of an IT or security team | Partner integration with Zero Trust for design guidance for technology areas and specializations | Apply Zero Trust protections to partner Microsoft cloud solutions. |
| Application developer | Develop using Zero Trust principles for application development design guidance and best practices | Apply Zero Trust protections to your application. |
- 登录 发表评论
- 23 次浏览
发布日期
星期四, 七月 25, 2024 - 16:08
最后修改
星期四, 七月 25, 2024 - 16:08
Article
最新内容
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago