category
摘要:要将零信任原则应用于Azure服务,您需要确定支持所需工作负载所需的基础架构组件集,然后将零信任原理应用于这些组件。
本系列文章帮助您使用多学科方法将零信任原则应用于Microsoft Azure中的服务。零信任是一种安全策略。它不是一种产品或服务,而是一种设计和实现以下安全原则的方法:
- 明确验证
- 使用最低权限访问
- 假设违约
实施零信任“从不信任,始终验证”的心态需要改变云基础设施、部署策略和实施。
这些文章向您展示了如何将零信任方法应用于这些新的或已部署的Azure服务:
- Azure IaaS overview
- Azure Virtual Desktop
- Azure Virtual WAN
- IaaS applications in Amazon Web Services
- Microsoft Sentinel and Microsoft Defender XDR
内容架构
以下是这组文章的内容架构,其中包含将零信任原则应用于Azure服务的平台和工作负载文章集。
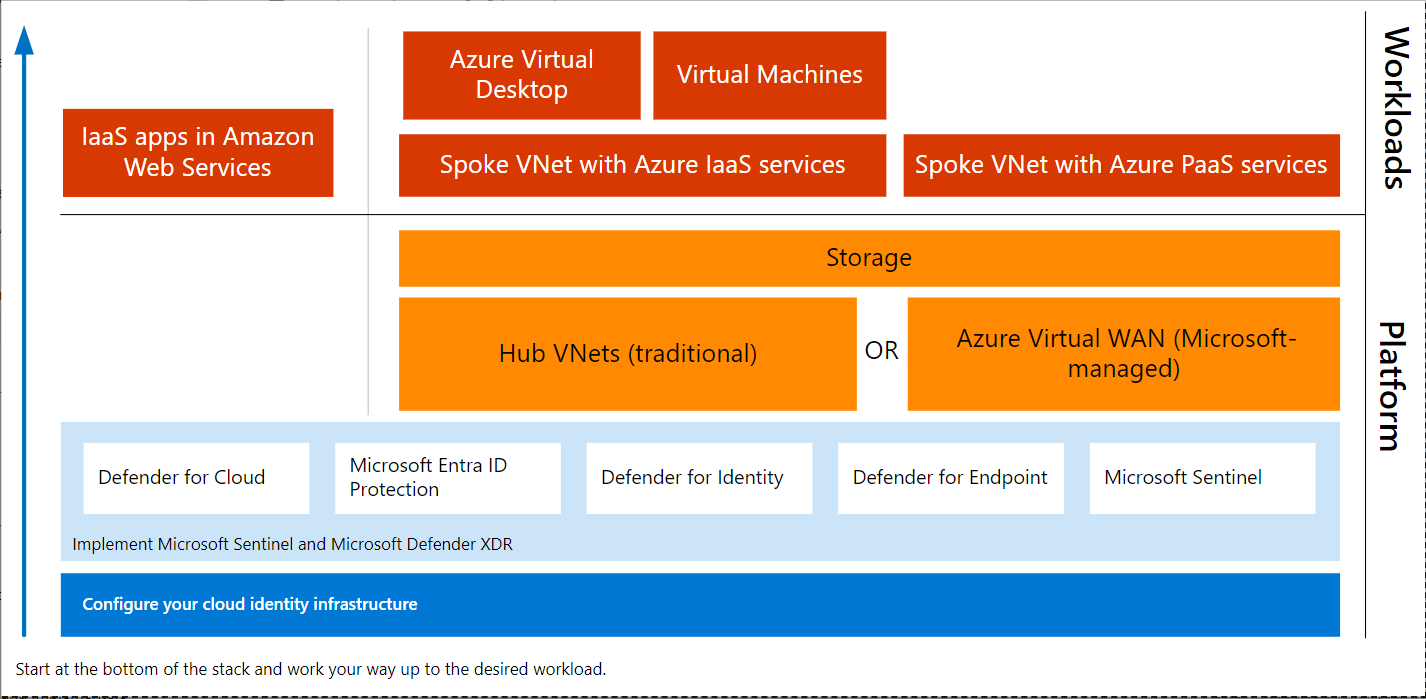
You apply the guidance in the articles in a stack from the bottom up.
| Workload | Platform set of articles (from the bottom up) |
|---|---|
| IaaS apps in Amazon Web Services (AWS) |
|
| Spoke VNet with Azure IaaS services |
|
| Azure Virtual Desktop or virtual machines |
|
It’s important to note that the guidance in this series of articles is more specific for this type of architecture than the guidance provided in the Cloud Adoption Framework and Azure landing zone architectures. If you have applied the guidance in either of these resources, be sure to also review this series of articles for additional recommendations.
Additional articles for Azure services
See these additional articles for applying Zero Trust principles to Azure services:
- For Azure IaaS:
- Azure Virtual Desktop
- Azure Virtual WAN
- IaaS applications in Amazon Web Services
- Protect Azure resources from cyberattacks
- Microsoft Sentinel and Microsoft Defender XDR
See these additional articles for applying Zero Trust principles to Azure networking:
- Encrypt your network traffic
- Segment your network traffic
- Gain visibility into your network traffic
- Discontinue legacy network security technology
References
Refer to the links below to learn about the various services and technologies mentioned in this article.
- What is Azure - Microsoft Cloud Services
- Introduction to Azure security
- Zero Trust implementation guidance
- Overview of the Microsoft cloud security benchmark
- Security baselines for Azure overview
- Building the first layer of defense with Azure security services
- Microsoft Cybersecurity Reference Architectures
Additional Zero Trust documentation
Use additional Zero Trust content based on a documentation set or the roles in your organization.
Documentation set
Follow this table for the best Zero Trust documentation sets for your needs.
| Documentation set | Helps you... | Roles |
|---|---|---|
| Adoption framework for phase and step guidance for key business solutions and outcomes | Apply Zero Trust protections from the C-suite to the IT implementation. | Security architects, IT teams, and project managers |
| Concepts and deployment objectives for general deployment guidance for technology areas | Apply Zero Trust protections aligned with technology areas. | IT teams and security staff |
| Zero Trust for small businesses | Apply Zero Trust principles to small business customers. | Customers and partners working with Microsoft 365 for business |
| Zero Trust Rapid Modernization Plan (RaMP) for project management guidance and checklists for easy wins | Quickly implement key layers of Zero Trust protection. | Security architects and IT implementers |
| Zero Trust deployment plan with Microsoft 365 for stepped and detailed design and deployment guidance | Apply Zero Trust protections to your Microsoft 365 tenant. | IT teams and security staff |
| Zero Trust for Microsoft Copilots for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Microsoft Copilots. | IT teams and security staff |
| Partner integration with Zero Trust for design guidance for technology areas and specializations | Apply Zero Trust protections to partner Microsoft cloud solutions. | Partner developers, IT teams, and security staff |
| Develop using Zero Trust principles for application development design guidance and best practices | Apply Zero Trust protections to your application. | Application developers |
Your role
Follow this table for the best documentation sets for your role in your organization.
| Role | Documentation set | Helps you... |
|---|---|---|
| Security architect IT project manager IT implementer |
Adoption framework for phase and step guidance for key business solutions and outcomes | Apply Zero Trust protections from the C-suite to the IT implementation. |
| Member of an IT or security team | Concepts and deployment objectives for general deployment guidance for technology areas | Apply Zero Trust protections aligned with technology areas. |
| Customer or partner for Microsoft 365 for business | Zero Trust for small businesses | Apply Zero Trust principles to small business customers. |
| Security architect IT implementer |
Zero Trust Rapid Modernization Plan (RaMP) for project management guidance and checklists for easy wins | Quickly implement key layers of Zero Trust protection. |
| Member of an IT or security team for Microsoft 365 | Zero Trust deployment plan with Microsoft 365 for stepped and detailed design and deployment guidance for Microsoft 365 | Apply Zero Trust protections to your Microsoft 365 tenant. |
| Member of an IT or security team for Microsoft Copilots | Zero Trust for Microsoft Copilots for stepped and detailed design and deployment guidance | Apply Zero Trust protections to Microsoft Copilots. |
| Partner developer or member of an IT or security team | Partner integration with Zero Trust for design guidance for technology areas and specializations | Apply Zero Trust protections to partner Microsoft cloud solutions. |
| Application developer | Develop using Zero Trust principles for application development design guidance and best practices | Apply Zero Trust protections to your application. |
- 登录 发表评论
- 28 次浏览
最新内容
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago