category
专用终结点是使用虚拟网络中的专用IP地址的网络接口。此网络接口将您安全地连接到由Azure private Link提供支持的服务。通过启用专用端点,您将服务带入虚拟网络。
该服务可以是Azure服务,例如:
- Azure存储
- Azure Cosmos数据库
- Azure SQL数据库
- 您自己的服务,使用专用链接服务。
专用终结点属性
专用终结点指定以下属性:
| Property | Description |
|---|---|
| Name | A unique name within the resource group. |
| Subnet | The subnet to deploy, where the private IP address is assigned. For subnet requirements, see the Limitations section later in this article. |
| Private-link resource | The private-link resource to connect by using a resource ID or alias, from the list of available types. A unique network identifier is generated for all traffic that's sent to this resource. |
| Target subresource | The subresource to connect. Each private-link resource type has various options to select based on preference. |
| Connection approval method | Automatic or manual. Depending on the Azure role-based access control permissions, your private endpoint can be approved automatically. If you're connecting to a private-link resource without Azure role based permissions, use the manual method to allow the owner of the resource to approve the connection. |
| Request message | You can specify a message for requested connections to be approved manually. This message can be used to identify a specific request. |
| Connection status |
A read-only property that specifies whether the private endpoint is active. Only private endpoints in an approved state can be used to send traffic. More available states:
|
在创建专用端点时,请考虑以下事项:
- 专用端点实现了客户之间的连接:
- 虚拟网络
- 区域对等虚拟网络
- 全球对等虚拟网络
- 使用VPN或Express Route的内部部署环境
- 由专用链接提供支持的服务
- 网络连接只能由连接到专用端点的客户端启动。服务提供商没有路由配置来创建到服务客户的连接。只能在一个方向上建立连接。
- 为专用端点的生命周期自动创建只读网络接口。接口从映射到专用链路资源的子网分配了一个动态专用IP地址。专用IP地址的值在专用端点的整个生命周期内保持不变。
- 专用终结点必须部署在与虚拟网络相同的区域和订阅中。
- 专用链路资源可以部署在与虚拟网络和专用端点不同的区域中。
- 可以使用相同的专用链接资源创建多个专用端点。对于使用通用DNS服务器配置的单个网络,建议的做法是为指定的专用链接资源使用单个专用端点。使用此做法可避免DNS解析中出现重复条目或冲突。
- 可以在同一虚拟网络中的相同或不同子网上创建多个专用终结点。在订阅中可以创建的专用终结点数量有限制。有关详细信息,请参阅Azure限制。
- 包含专用链接资源的订阅必须向Microsoft网络资源提供商注册。包含专用终结点的订阅也必须向Microsoft网络资源提供程序注册。有关更多信息,请参阅“Azure资源提供商”。
专用链接资源
专用链接资源是指定的专用终结点的目标。下表列出了支持专用终结点的可用资源:
| Private-link resource name | Resource type | Sub-resources |
|---|---|---|
| Application Gateway | Microsoft.Network/applicationgateways | Frontend IP Configuration name |
| Azure AI services | Microsoft.CognitiveServices/accounts | account |
| Azure API for FHIR (Fast Healthcare Interoperability Resources) | Microsoft.HealthcareApis/services | fhir |
| Azure App Configuration | Microsoft.Appconfiguration/configurationStores | configurationStores |
| Azure App Service | Microsoft.Web/hostingEnvironments | hosting environment |
| Azure App Service | Microsoft.Web/sites | sites |
| Azure Automation | Microsoft.Automation/automationAccounts | Webhook, DSCAndHybridWorker |
| Azure Backup | Microsoft.RecoveryServices/vaults | AzureBackup, AzureSiteRecovery |
| Azure Batch | Microsoft.Batch/batchAccounts | batchAccount, nodeManagement |
| Azure Cache for Redis | Microsoft.Cache/Redis | redisCache |
| Azure Cache for Redis Enterprise | Microsoft.Cache/redisEnterprise | redisEnterprise |
| Azure AI Search | Microsoft.Search/searchServices | searchService |
| Azure Container Registry | Microsoft.ContainerRegistry/registries | registry |
| Azure Cosmos DB | Microsoft.AzureCosmosDB/databaseAccounts | SQL, MongoDB, Cassandra, Gremlin, Table |
| Azure Cosmos DB for PostgreSQL | Microsoft.DBforPostgreSQL/serverGroupsv2 | coordinator |
| Azure Cosmos DB for MongoDB vCore | Microsoft.DocumentDb/mongoClusters | mongoCluster |
| Azure Data Explorer | Microsoft.Kusto/clusters | cluster |
| Azure Data Factory | Microsoft.DataFactory/factories | dataFactory |
| Azure Database for MariaDB | Microsoft.DBforMariaDB/servers | mariadbServer |
| Azure Database for MySQL - Single Server | Microsoft.DBforMySQL/servers | mysqlServer |
| Azure Database for MySQL- Flexible Server | Microsoft.DBforMySQL/flexibleServers | mysqlServer |
| Azure Database for PostgreSQL - Single server | Microsoft.DBforPostgreSQL/servers | postgresqlServer |
| Azure Database for PostgreSQL - Flexible server | Microsoft.DBforPostgreSQL/flexibleServers | postgresqlServer |
| Azure Databricks | Microsoft.Databricks/workspaces | databricks_ui_api, browser_authentication |
| Azure Device Provisioning Service | Microsoft.Devices/provisioningServices | iotDps |
| Azure Digital Twins | Microsoft.DigitalTwins/digitalTwinsInstances | API |
| Azure Event Grid | Microsoft.EventGrid/domains | domain |
| Azure Event Grid | Microsoft.EventGrid/topics | topic |
| Azure Event Hub | Microsoft.EventHub/namespaces | namespace |
| Azure File Sync | Microsoft.StorageSync/storageSyncServices | File Sync Service |
| Azure HDInsight | Microsoft.HDInsight/clusters | cluster |
| Azure IoT Central | Microsoft.IoTCentral/IoTApps | IoTApps |
| Azure IoT Hub | Microsoft.Devices/IotHubs | iotHub |
| Azure Key Vault | Microsoft.KeyVault/vaults | vault |
| Azure Key Vault HSM (hardware security module) | Microsoft.Keyvault/managedHSMs | HSM |
| Azure Kubernetes Service - Kubernetes API | Microsoft.ContainerService/managedClusters | management |
| Azure Machine Learning | Microsoft.MachineLearningServices/registries | amlregistry |
| Azure Machine Learning | Microsoft.MachineLearningServices/workspaces | amlworkspace |
| Azure Managed Disks | Microsoft.Compute/diskAccesses | managed disk |
| Azure Media Services | Microsoft.Media/mediaservices | keydelivery, liveevent, streamingendpoint |
| Azure Migrate | Microsoft.Migrate/assessmentProjects | project |
| Azure Monitor Private Link Scope | Microsoft.Insights/privatelinkscopes | azuremonitor |
| Azure Relay | Microsoft.Relay/namespaces | namespace |
| Azure Service Bus | Microsoft.ServiceBus/namespaces | namespace |
| Azure SignalR Service | Microsoft.SignalRService/SignalR | signalr |
| Azure SignalR Service | Microsoft.SignalRService/webPubSub | webpubsub |
| Azure SQL Database | Microsoft.Sql/servers | SQL Server (sqlServer) |
| Azure SQL Managed Instance | Microsoft.Sql/managedInstances | managedInstance |
| Azure Static Web Apps | Microsoft.Web/staticSites | staticSites |
| Azure Storage | Microsoft.Storage/storageAccounts | Blob (blob, blob_secondary) Table (table, table_secondary) Queue (queue, queue_secondary) File (file, file_secondary) Web (web, web_secondary) Dfs (dfs, dfs_secondary) |
| Azure Synapse | Microsoft.Synapse/privateLinkHubs | web |
| Azure Synapse Analytics | Microsoft.Synapse/workspaces | Sql, SqlOnDemand, Dev |
| Azure Virtual Desktop - host pools | Microsoft.DesktopVirtualization/hostpools | connection |
| Azure Virtual Desktop - workspaces | Microsoft.DesktopVirtualization/workspaces | feed global |
| Device Update for IoT Hub | Microsoft.DeviceUpdate/accounts | DeviceUpdate |
| Microsoft Purview | Microsoft.Purview/accounts | account |
| Microsoft Purview | Microsoft.Purview/accounts | portal |
| Power BI | Microsoft.PowerBI/privateLinkServicesForPowerBI | Power BI |
| Private Link service (your own service) | Microsoft.Network/privateLinkServices | empty |
| Resource Management Private Links | Microsoft.Authorization/resourceManagementPrivateLinks | ResourceManagement |
笔记
只能在通用v2(GPv2)存储帐户上创建专用终结点。专用端点的网络安全
当您使用专用端点时,流量会被保护到专用链接资源。该平台验证网络连接,只允许那些访问指定专用链接资源的连接。若要访问同一Azure服务中的更多子资源,需要更多具有相应目标的专用终结点。例如,在Azure存储的情况下,您需要单独的专用端点来访问文件和blob子资源。
专用终结点为Azure服务提供私人可访问的IP地址,但不一定限制对其的公共网络访问。但是,所有其他Azure服务都需要额外的访问控制。这些控件为您的资源提供了一个额外的网络安全层,提供了有助于防止访问与专用链接资源相关联的Azure服务的保护。
专用端点支持网络策略。网络策略支持网络安全组(NSG)、用户定义路由(UDR)和应用程序安全组(ASG)。有关为专用终结点启用网络策略的详细信息,请参阅管理专用终结点的网络策略。要将ASG与专用端点一起使用,请参阅使用专用端点配置应用程序安全组(ASG)。
使用审批工作流访问专用链接资源
您可以使用以下连接审批方法连接到专用链接资源:
- 自动批准:当您拥有或拥有特定专用链接资源的权限时,请使用此方法。所需权限基于以下格式的专用链接资源类型:
Microsoft.<Provider>/<resource_type>/privateEndpointConnectionsApproval/action
- 手动请求:当您没有所需的权限并希望请求访问时,请使用此方法。将启动审批工作流。专用端点和以后的专用端点连接是在挂起状态下创建的。专用链接资源所有者负责批准连接。审批后,私有端点可以正常发送流量,如以下审批流程图所示:
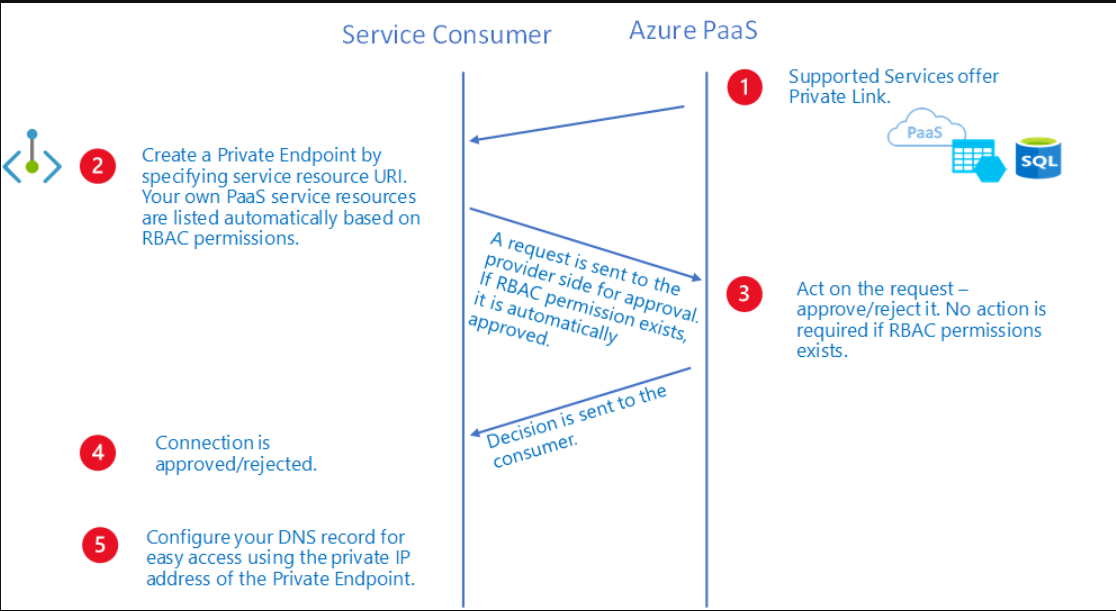
通过专用端点连接,专用链接资源所有者可以:
- 查看所有专用终结点连接详细信息。
- 批准专用终结点连接。相应的专用端点能够向专用链路资源发送流量。
- 拒绝专用终结点连接。相应的专用端点将更新以反映状态。
- 删除任何状态下的专用端点连接。相应的专用端点将更新为断开连接状态以反映该操作。专用端点所有者此时只能删除资源。
笔记
只有处于“已批准”状态的专用终结点才能向指定的专用链接资源发送流量。使用别名连接
别名是当服务所有者在标准负载均衡器后面创建专用链接服务时生成的唯一名称。服务所有者可以与服务的使用者脱机共享此别名。
使用者可以通过使用资源URI或别名来请求与专用链接服务的连接。若要使用别名进行连接,请使用手动连接审批方法创建专用终结点。要使用手动连接审批方法,请在专用端点创建流期间将手动请求参数设置为True。有关更多信息,请参阅新建AzPrivateEndpoint和创建az网络专用端点。
笔记
如果允许在提供商端列出消费者的订阅,则可以自动批准此手动请求。要了解更多信息,请转到控制服务访问。DNS配置
用于连接到专用链接资源的DNS设置非常重要。现有Azure服务可能已经具有DNS配置,当您通过公共端点进行连接时可以使用该配置。要通过专用端点连接到同一服务,需要单独的DNS设置,通常通过专用DNS区域进行配置。当您为连接使用完全限定域名(FQDN)时,请确保DNS设置正确。设置必须解析为专用终结点的专用IP地址。
与专用终结点关联的网络接口包含配置DNS所需的信息。该信息包括专用链路资源的FQDN和专用IP地址。
有关建议为专用端点配置DNS的完整详细信息,请参阅专用端点DNS配置。
局限性
以下信息列出了使用专用端点的已知限制:
静态IP地址
| Limitation | Description |
|---|---|
| Static IP address configuration currently unsupported. | Azure Kubernetes Service (AKS) Azure Application Gateway HD Insight Recovery Services Vaults Third party Private Link services |
网络安全组
| Limitation | Description |
|---|---|
| Effective routes and security rules unavailable for private endpoint network interface. | Effective routes and security rules won't be displayed for the private endpoint NIC in the Azure portal. |
| NSG flow logs unsupported. | NSG flow logs unavailable for inbound traffic destined for a private endpoint. |
| No more than 50 members in an Application Security Group. | Fifty is the number of IP Configurations that can be tied to each respective ASG that's coupled to the NSG on the private endpoint subnet. Connection failures may occur with more than 50 members. |
| Destination port ranges supported up to a factor of 250 K. | Destination port ranges are supported as a multiplication SourceAddressPrefixes, DestinationAddressPrefixes, and DestinationPortRanges. Example inbound rule: One source * one destination * 4K portRanges = 4K Valid 10 sources * 10 destinations * 10 portRanges = 1 K Valid 50 sources * 50 destinations * 50 portRanges = 125 K Valid 50 sources * 50 destinations * 100 portRanges = 250 K Valid 100 sources * 100 destinations * 100 portRanges = 1M Invalid, NSG has too many sources/destinations/ports. |
| Source port filtering is interpreted as * | Source port filtering isn't actively used as valid scenario of traffic filtering for traffic destined to a private endpoint. |
| Feature unavailable in select regions. | Currently unavailable in the following regions: West India Australia Central 2 South Africa West Brazil Southeast All Government regions All China regions |
NSG更多注意事项
拒绝来自专用终结点的出站流量不是有效的方案,因为服务提供商无法发起流量。- 以下服务可能要求在使用专用端点和添加NSG安全筛选器时打开所有目标端口:
- Azure Cosmos DB-有关更多信息,请参阅服务端口范围。
- Azure Cosmos DB-有关更多信息,请参阅服务端口范围。
UDR
| Limitation | Description |
|---|---|
| SNAT is recommended always. | Due to the variable nature of the private endpoint data-plane, it's recommended to SNAT traffic destined to a private endpoint to ensure return traffic is honored. |
| Feature unavailable in select regions. | Currently unavailable in the following regions: West India Australia Central 2 South Africa West Brazil Southeast |
应用程序安全组
| Limitation | Description |
|---|---|
| Feature unavailable in select regions. | Currently unavailable in the following regions: West India Australia Central 2 South Africa West Brazil Southeast |
接下来的步骤
有关专用端点和专用链接的更多信息,请参阅什么是Azure专用链接?。
要开始为web应用创建专用端点,请参阅快速启动:使用Azure门户创建专用端点。
- 登录 发表评论
- 70 次浏览
Tags
最新内容
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago