category
在Microsoft Entra ID中有两种应用程序的表示:
- 应用程序对象——尽管存在例外,但应用程序对象可以被视为应用程序的定义。
- 服务主体——可以看作是应用程序的实例。服务主体通常引用一个应用程序对象,一个应用程序对象可以被多个服务主体跨目录引用。
什么是应用程序对象,它们来自哪里?
您可以通过应用程序注册体验在Microsoft Entra管理中心管理应用程序对象。应用程序对象将应用程序描述为Microsoft Entra ID,并且可以视为应用程序的定义,允许服务知道如何根据其设置向应用程序发出令牌。应用程序对象将只存在于它的主目录中,即使它是支持其他目录中的服务主体的多租户应用程序。应用程序对象可以包括(但不限于)以下任何内容:
- 名称、徽标和出版商
- 重定向的uri
- 秘密(用于验证应用程序的对称和/或非对称密钥)
- API依赖(OAuth)
- 已发布的api /资源/作用域(OAuth)
- 应用程序角色
- 单点登录(SSO)元数据和配置
- 用户供应元数据和配置
- 代理元数据和配置
应用程序对象可以通过多种途径创建,包括:
- 在Microsoft Entra管理中心进行应用程序注册
- 使用Visual Studio创建一个新应用程序,并将其配置为使用Microsoft Entra身份验证
- 当管理员从应用库中添加应用时(这也会创建一个服务主体)
- 使用微软图形API或PowerShell创建一个新的应用程序
- 其他的还包括Azure中的各种开发人员体验和跨开发人员中心的API资源管理器体验
什么是服务主体,它们来自哪里?
您可以通过企业应用程序体验在Microsoft Entra管理中心管理服务主体。服务主体管理连接到Microsoft Entra ID的应用程序,可以将其视为目录中应用程序的实例。对于任何给定的应用程序,它最多可以有一个应用程序对象(在“home”目录中注册),以及一个或多个服务主体对象,这些对象表示应用程序在其运行的每个目录中的实例。
服务主体可以包括:
- 通过应用程序ID属性返回到应用程序对象的引用
- 本地用户和组应用程序角色分配的记录
- 授予应用程序的本地用户和管理员权限记录
- 例如:应用程序访问特定用户电子邮件的权限
- 本地策略记录,包括条件访问策略
- 用程序的备用本地设置的记录
- 索赔转换规则
- 属性映射(用户发放)
- 特定于目录的应用程序角色(如果应用程序支持自定义角色)
- 特定于目录的名称或标志
与应用程序对象一样,服务主体也可以通过多种途径创建,包括:
- 当用户登录到与Microsoft Entra ID集成的第三方应用程序时
- 在登录期间,用户被要求授予应用程序访问其配置文件和其他权限的权限。第一个同意的人将导致一个代表应用程序的服务主体被添加到目录中。
- 当用户登录微软的在线服务,如微软365。
- 当您订阅Microsoft 365或开始试用时,将在表示用于交付与Microsoft 365相关的所有功能的各种服务的目录中创建一个或多个服务主体。
- 一些Microsoft 365服务,如SharePoint,在持续的基础上创建服务主体,以允许组件(包括工作流)之间的安全通信。
- 当管理员从应用库中添加应用时(这也会创建一个底层应用对象)
- 添加应用程序以使用Microsoft Entra应用程序代理
- 使用SAML或密码单点登录连接应用程序
- 通过微软图形API或PowerShell编程
应用程序对象和服务主体是如何相互关联的?
应用程序的主目录中有一个应用程序对象,该对象由应用程序运行的每个目录(包括应用程序的主目录)中的一个或多个服务主体引用。
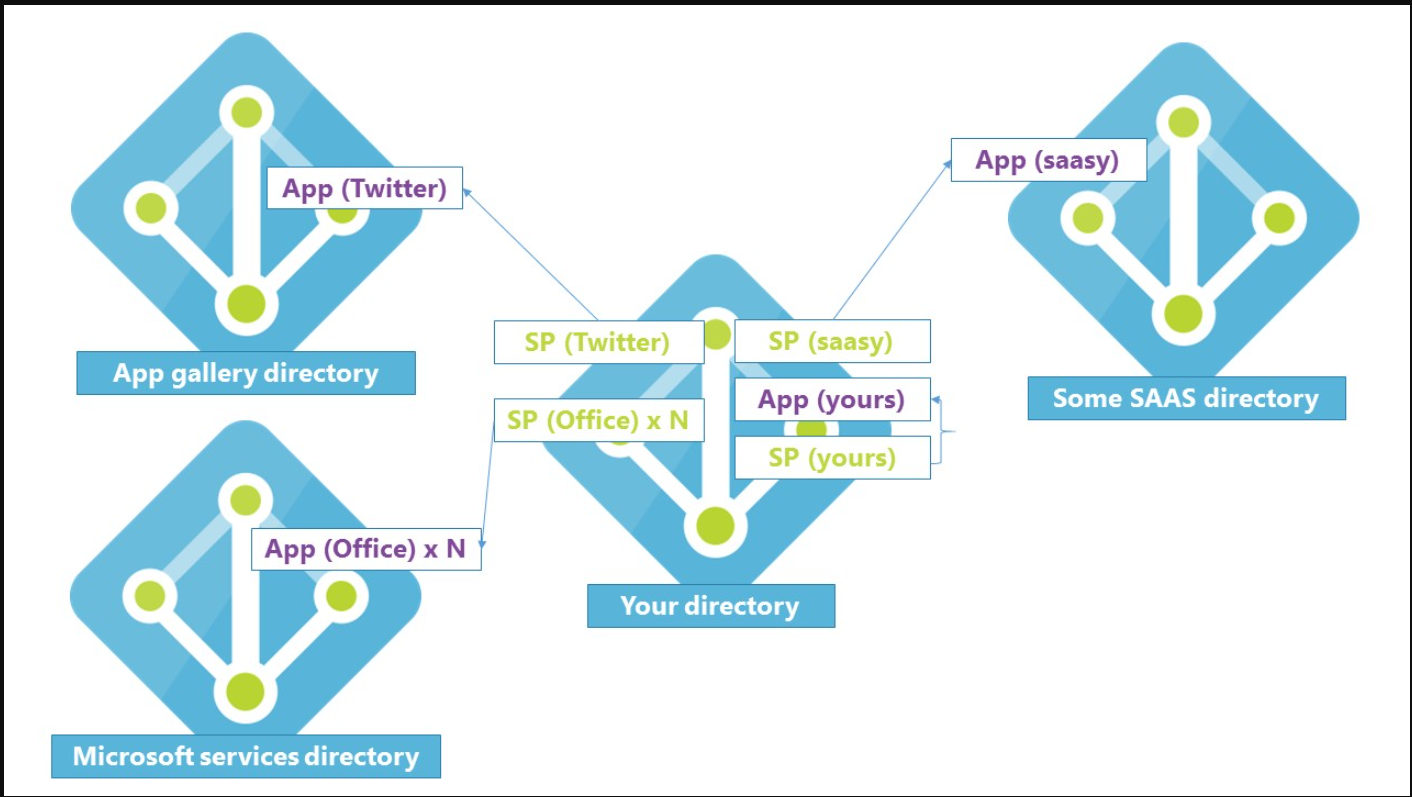
显示应用对象和服务主体之间的关系
在前面的图表中,微软内部维护了两个用于发布应用程序的目录(如图所示):
- 一个是Microsoft Apps (Microsoft services目录)
- 一个用于预集成的第三方应用程序(应用程序库目录)
Application publishers/vendors who integrate with Microsoft Entra ID are required to have a publishing directory (shown on the right as "Some software as a service (SaaS) Directory"). Applications that you add yourself (represented as App (yours) in the diagram) include: Applications are added to Microsoft Entra ID to use one or more of the services it provides including: By default all users in your directory have rights to register application objects that they're developing and discretion over which applications they share/give access to their organizational data through consent. If a person is the first user in your directory to sign in to an application and grant consent, that will create a service principal in your tenant. Otherwise, the consent grant information will be stored on the existing service principal. Allowing users to register and consent to applications might initially sound concerning, but keep the following reasons in mind: If you still want to prevent users in your directory from registering applications and from signing in to applications without administrator approval, there are two settings that you can change to turn off those capabilities: To change the user consent settings in your organization, see Configure how users consent to applications. To prevent users from registering their own applications:
Notes and exceptions
为什么应用程序与Microsoft Entra ID集成?
谁有权限向我的Microsoft Entra实例添加应用程序?
- 登录 发表评论
- 25 次浏览
Tags
最新内容
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago
- 1 month ago