category
您可以使用各种Azure服务构建整个IT基础设施来运行您的组织。Azure还提供安全服务来保护您的基础设施。通过使用Azure安全服务,您可以改善IT环境的安全状况。您可以根据Microsoft的建议实施架构良好的解决方案,从而减少漏洞并避免漏洞泄露。
一些安全服务会收取费用,而另一些则不收取额外费用。免费服务包括网络安全组(NSG)、存储加密、TLS/SSL、共享访问签名令牌以及许多其他服务。本文涵盖了此类服务。
这篇文章是五篇文章中的第三篇。要回顾本系列的前两篇文章,包括如何将威胁映射到IT环境的介绍和回顾,请参阅以下文章:
使用Azure监控集成安全组件
将威胁映射到您的IT环境
潜在用例
本文根据每个Azure服务介绍Azure安全服务。通过这种方式,您可以想到针对资源的特定威胁——虚拟机(VM)、操作系统、Azure网络、应用程序——或者可能危及用户和密码的攻击。然后使用本文中的图表来帮助您了解使用哪些Azure安全服务来保护资源和用户身份免受该类型的威胁。
架构
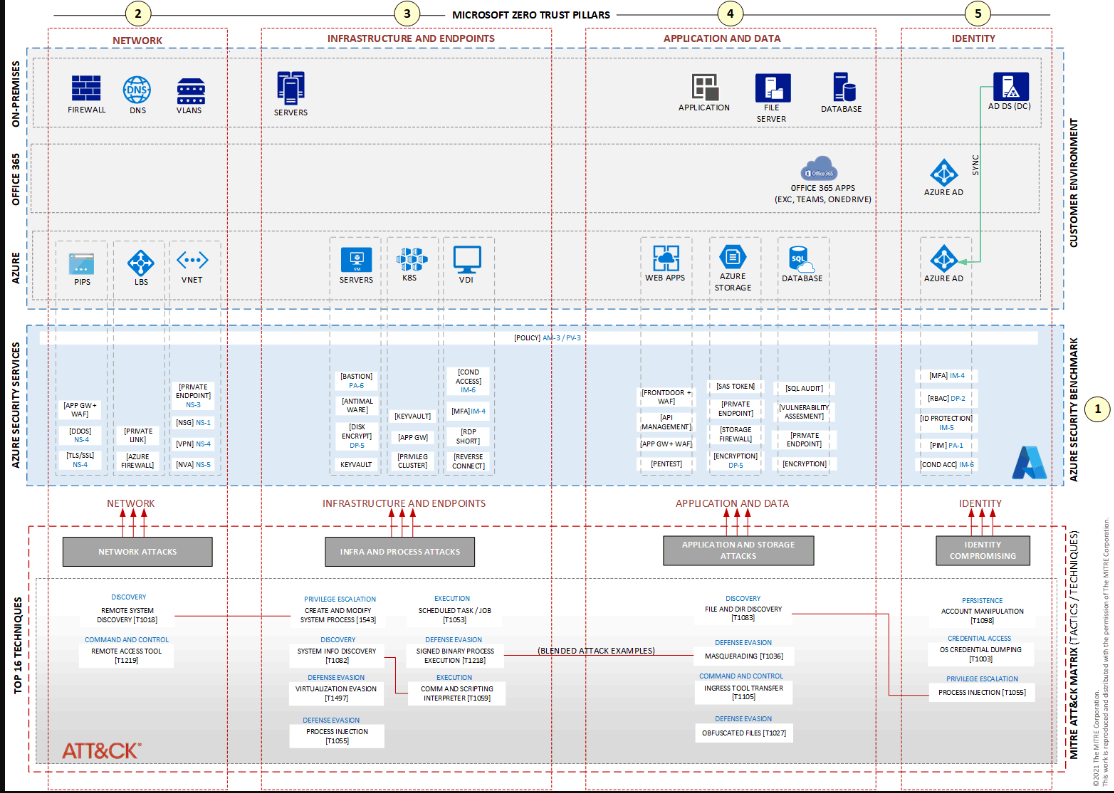
内部部署资源、Microsoft 365和Azure的服务以及MITRE ATTACK矩阵分类的16种威胁的图表。
Download a Visio file of this architecture.
©2021 MITRE公司。本作品经MITRE公司许可复制和分发。
此图中的Azure安全层基于Azure安全基准(ASB)v3,这是一组通过Azure策略实现的安全规则。ASB基于CIS互联网安全中心和国家标准与技术研究所的规则。有关ASB的更多信息,请参阅Azure Security Benchmark v3概述。
该图并不包含所有可用的Azure安全服务,但它显示了组织最常用的安全服务。体系结构图中标识的所有安全服务都可以根据您的IT环境和组织的安全要求以任何组合的方式协同工作。
工作流
本节介绍图中显示的组件和服务。除了缩写标签外,其中许多还标有ASB控制代码。控制代码对应于“控制”中列出的控制域。
AZURE安全基准
每个安全控件都指一个或多个特定的Azure安全服务。本文中的体系结构参考根据ASB文档显示了其中一些及其控制编号。控件包括:
- 网络安全
- 身份管理
- 特权访问
- 数据保护
- 资产管理
- 日志记录和威胁检测
- 事件响应
- 姿态和漏洞管理
- 端点安全
- 备份和恢复
- DevOps安全
- 治理和战略
有关安全控制的更多信息,请参阅Azure安全基准测试概述(v3)。
网络
下表描述了图中的网络服务。
| Label | Description | Documentation |
|---|---|---|
| NSG | A free service that you attach to a network interface or subnet. An NSG allows you to filter TCP or UDP protocol traffic by using IP address ranges and ports for inbound and outbound connections. | Network security groups |
| VPN | A virtual private network (VPN) gateway that delivers a tunnel with IPSEC (IKE v1/v2) protection. | VPN Gateway |
| AZURE FIREWALL | A platform as a service (PaaS) that delivers protection in layer 4 and is attached to an entire virtual network. | What is Azure Firewall? |
| APP GW + WAF | Azure Application Gateway with Web Application Firewall (WAF). Application Gateway is a load balancer for web traffic that works in layer 7 and adds WAF to protect applications that use HTTP and HTTPS. | What is Azure Application Gateway? |
| NVA | Network Virtual Appliance (NVA), a virtual security services from the marketplace that is provisioned on VMs on Azure. | Network Virtual Appliances |
| DDOS | DDoS protection implemented on the virtual network to help you mitigate different types of DDoS attacks. | Azure DDoS Network Protection overview |
| TLS/SSL | TLS/SSL deliver encryption in transit for most Azure services that exchange information, such as Azure Storage and Web Apps. | Configure end-to-end TLS by using Application Gateway with PowerShell |
| PRIVATE LINK | Service that allows you to create a private network for an Azure service that initially is exposed to the internet. | What is Azure Private Link? |
| PRIVATE ENDPOINT | Creates a network interface and attaches it to the Azure service. Private Endpoint is part of Private Link. This configuration lets the service, by using a private endpoint, be part of your virtual network. | What is a private endpoint? |
基础设施和端点
下表描述了图中所示的基础结构和端点服务。
| Label | Description | Documentation |
|---|---|---|
| BASTION | Bastion provides jump server functionality. This service allows you to access your VMs through remote desktop protocol (RDP) or SSH without exposing your VMs to the internet. | What is Azure Bastion? |
| ANTIMALWARE | Microsoft Defender provides anti-malware service and is part of Windows 10, Windows 11, Windows Server 2016, and Windows Server 2019. | Microsoft Defender Antivirus in Windows |
| DISK ENCRYPT | Disk Encryption allows you to encrypt the disk of a VM. | Azure Disk Encryption for Windows VMs |
| KEYVAULT | Key Vault, a service to store keys, secrets, and certificates with FIPS 140-2 Level 2 or 3. | Azure Key Vault basic concepts |
| RDP SHORT | Azure Virtual Desktop RDP Shortpath. This feature allows remote users to connect to the Virtual Desktop service from a private network. | Azure Virtual Desktop RDP Shortpath for managed networks |
| REVERSE CONNECT | A built-in security feature from Azure Virtual Desktop. Reverse connect guarantees that remote users receive only pixel streams and don't reach the host VMs. | Understanding Azure Virtual Desktop network connectivity |
应用程序和数据
下表描述了图中显示的应用程序和数据服务。
| Label | Description | Documentation |
|---|---|---|
| FRONTDOOR + WAF | A content delivery network (CDN). Front Door combines multiple points of presence to deliver a better connection for users who access the service and adds WAF. | What is Azure Front Door? |
| API MANAGEMENT | A service that delivers security for API calls and manages APIs across environments. | About API Management |
| PENTEST | A set of best practices to execute a penetration test in your environment, including Azure resources. | Penetration testing |
| STORAGE SAS TOKEN | A shared access token to allow others to access your Azure storage account. | Grant limited access to Azure Storage resources using shared access signatures (SAS) |
| PRIVATE ENDPOINT | Create a network interface and attach it to your storage account to configure it inside a private network on Azure. | Use private endpoints for Azure Storage |
| STORAGE FIREWALL | Firewall that allows you to set a range of IP addresses that can access your storage account. | Configure Azure Storage firewalls and virtual networks |
| ENCRYPTION (Azure Storage) |
Protects your storage account with encryption at rest. | Azure Storage encryption for data at rest |
| SQL AUDIT | Tracks database events and writes them to an audit log in your Azure storage account. | Auditing for Azure SQL Database and Azure Synapse Analytics |
| VULNERABILITY ASSESSMENT | Service that helps you discover, track, and remediate potential database vulnerabilities. | SQL vulnerability assessment helps you identify database vulnerabilities |
| ENCRYPTION (Azure SQL) |
Transparent data encryption (TDE) helps protect Azure SQL database services by encrypting data at rest. | Transparent data encryption for SQL Database, SQL Managed Instance, and Azure Synapse Analytics |
身份
下表描述了图中显示的身份服务。
| Label | Description | Documentation |
|---|---|---|
| RBAC | Azure role-based access control (Azure RBAC) helps you manage access to Azure services by using granular permissions that are based on users' Microsoft Entra credentials. | What is Azure role-based access control (Azure RBAC)? |
| MFA | Multifactor authentication offers additional types of authentication beyond user names and passwords. | How it works: Microsoft Entra multifactor authentication |
| ID PROTECTION | Identity Protection, a security service from Microsoft Entra ID, analyzes trillions of signals per day to identify and protect users from threats. | What is Identity Protection? |
| PIM | Privileged Identity Management (PIM), a security service from Microsoft Entra ID. It helps you to provide superuser privileges temporarily for Microsoft Entra ID (for example, Global Admin) and Azure subscriptions (for example, owner or contributor). | What is Microsoft Entra Privileged Identity Management? |
| COND ACC | Conditional Access is an intelligent security service that uses policies that you define for various conditions to block or grant access to users. | What is Conditional Access? |
组件
本文中的示例体系结构使用以下Azure组件:
- Microsoft Entra ID是一种基于云的身份和访问管理服务。Microsoft Entra ID可帮助您的用户访问外部资源,如Microsoft 365、Azure门户和数千个其他SaaS应用程序。它还可以帮助他们访问内部资源,如企业内部网上的应用程序。
- Azure虚拟网络是Azure中私有网络的基本构建块。虚拟网络使许多类型的Azure资源能够安全地相互通信、互联网和本地网络。虚拟网络提供了一个虚拟网络,该网络受益于Azure的基础设施,如规模、可用性和隔离。
- Azure负载平衡器是一种高性能、低延迟的第4层负载平衡服务(入站和出站),适用于所有UDP和TCP协议。它的构建旨在每秒处理数百万个请求,同时确保您的解决方案具有高可用性。Azure负载平衡器是区域冗余的,可确保跨可用性区域的高可用性。
- 虚拟机是Azure提供的几种按需、可扩展的计算资源之一。Azure虚拟机(VM)为您提供了虚拟化的灵活性,而无需购买和维护运行它的物理硬件。
- Azure Kubernetes服务(AKS)是一种完全托管的Kubernets服务,用于部署和管理容器化应用程序。AKS提供无服务器Kubernetes、持续集成/持续交付(CI/CD)以及企业级安全和治理。
- Azure虚拟桌面是一种在云上运行的桌面和应用程序虚拟化服务,为远程用户提供桌面。
- 应用程序服务Web应用程序是一种基于HTTP的服务,用于托管Web应用程序、REST API和移动后端。您可以使用自己喜欢的语言进行开发,应用程序可以在基于Windows和Linux的环境中轻松运行和扩展。
- Azure存储是云中各种数据对象的高可用性、大规模可扩展性、持久性和安全存储,包括对象、blob、文件、磁盘、队列和表存储。写入Azure存储帐户的所有数据都由该服务加密。Azure存储为您提供了对谁有权访问您的数据的细粒度控制。
- Azure SQL数据库是一个完全管理的PaaS数据库引擎,它处理大多数数据库管理功能,如升级、修补、备份和监控。它在没有用户参与的情况下提供这些功能。SQL数据库提供了一系列内置的安全和法规遵从性功能,以帮助您的应用程序满足安全和法规要求。
Microsoft has more documentation that can help you secure your IT environment, and the following articles can be particularly helpful: In the following resources, you can find more information about the services, technologies, and terminologies that are mentioned in this article: For more details about this reference architecture, see the other articles in this series:
Next steps
Related resources
- 登录 发表评论
- 22 次浏览
最新内容
- 2 weeks 3 days ago
- 2 weeks 3 days ago
- 2 weeks 3 days ago
- 2 weeks 3 days ago
- 2 weeks 3 days ago
- 2 weeks 3 days ago
- 2 weeks 3 days ago
- 2 weeks 3 days ago
- 2 weeks 3 days ago
- 2 weeks 3 days ago