category
If you're new to Azure, you may find it a little challenging to understand all the different roles in Azure. This article helps explain the following roles and when you would use each:
- Azure roles
- Microsoft Entra roles
- Classic subscription administrator roles
How the roles are related
为了更好地了解Azure中的角色,了解一些历史会有所帮助。Azure最初发布时,对资源的访问仅由三个管理员角色管理:帐户管理员、服务管理员和联合管理员。后来,添加了Azure基于角色的访问控制(Azure RBAC)。Azure RBAC是一个较新的授权系统,提供对Azure资源的细粒度访问管理。Azure RBAC包含许多内置角色,可以在不同的范围内分配,并允许您创建自己的自定义角色。要管理Microsoft Entra ID中的资源,如用户、组和域,有几个Microsoft Entra角色。
下图是Azure角色、Microsoft Entra角色和经典订阅管理员角色之间关系的高级视图。
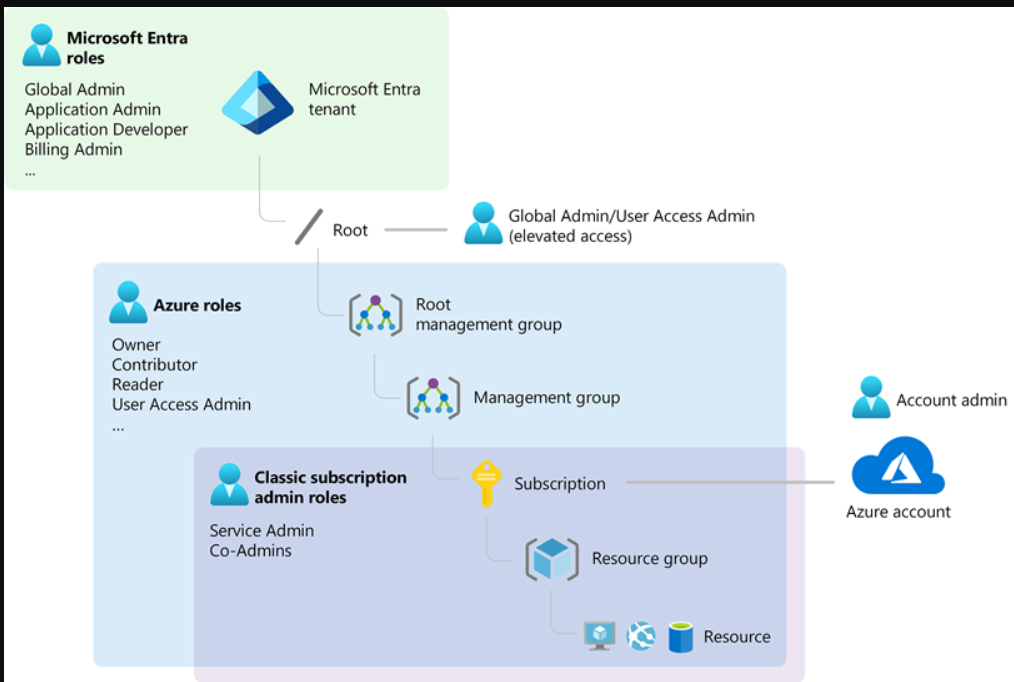
Azure roles
Azure RBAC is an authorization system built on Azure Resource Manager that provides fine-grained access management to Azure resources, such as compute and storage. Azure RBAC includes over 100 built-in roles. There are five fundamental Azure roles. The first three apply to all resource types:
| Azure role | Permissions | Notes |
|---|---|---|
| Owner |
|
The Service Administrator and Co-Administrators are assigned the Owner role at the subscription scope Applies to all resource types. |
| Contributor |
|
Applies to all resource types. |
| Reader |
|
Applies to all resource types. |
| Role Based Access Control Administrator |
|
|
| User Access Administrator |
|
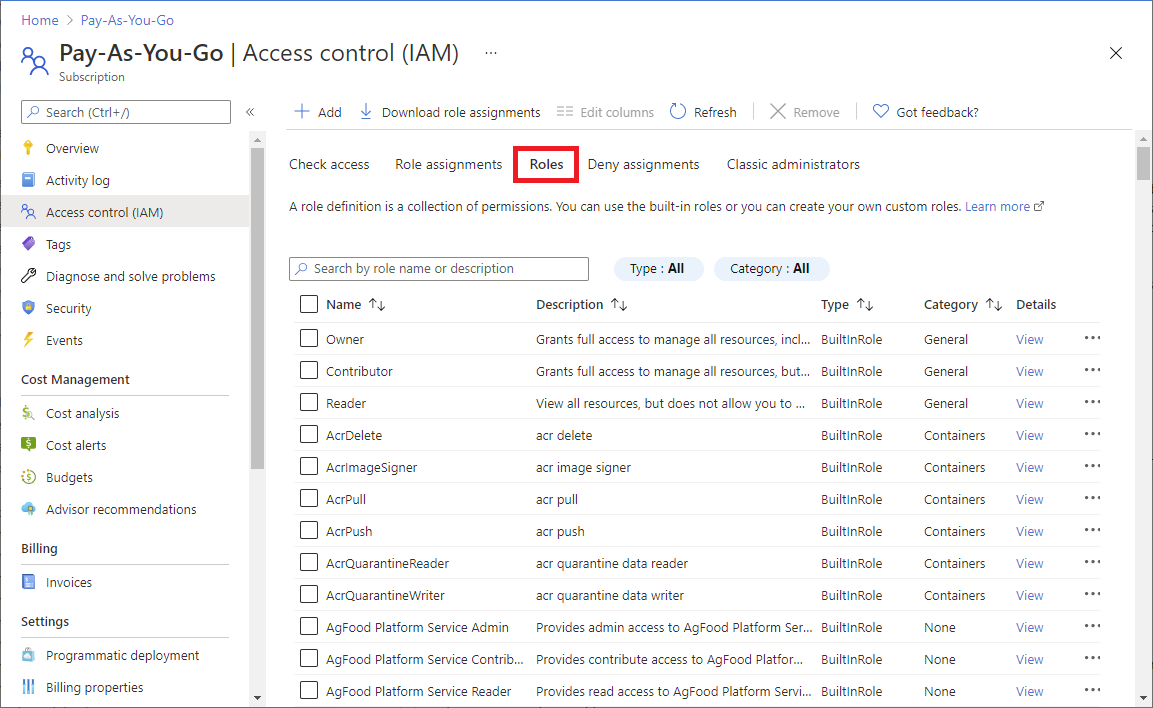
The rest of the built-in roles allow management of specific Azure resources. For example, the Virtual Machine Contributor role allows the user to create and manage virtual machines. For a list of all the built-in roles, see Azure built-in roles.
Only the Azure portal and the Azure Resource Manager APIs support Azure RBAC. Users, groups, and applications that are assigned Azure roles can't use the Azure classic deployment model APIs.
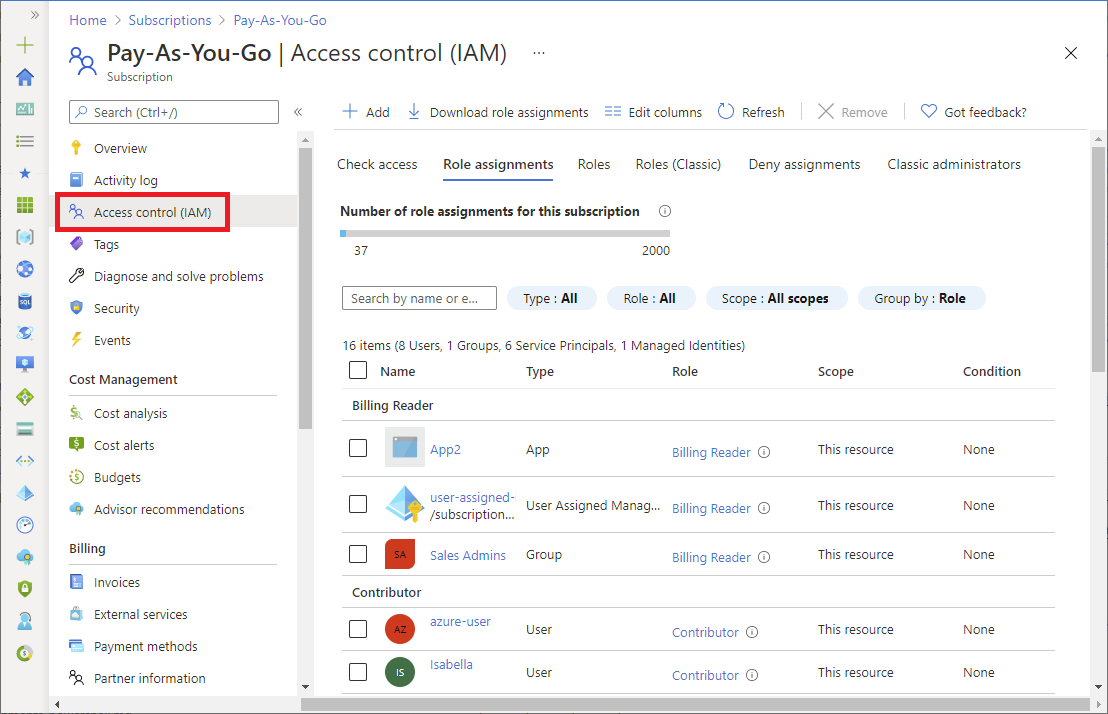
In the Azure portal, role assignments using Azure RBAC appear on the Access control (IAM) page. This page can be found throughout the portal, such as management groups, subscriptions, resource groups, and various resources.
When you click the Roles tab, you'll see the list of built-in and custom roles.
For more information, see Assign Azure roles using the Azure portal.
Microsoft Entra roles
Microsoft Entra roles are used to manage Microsoft Entra resources in a directory such as create or edit users, assign administrative roles to others, reset user passwords, manage user licenses, and manage domains. The following table describes a few of the more important Microsoft Entra roles.
| Microsoft Entra role | Permissions | Notes |
|---|---|---|
| Global Administrator |
|
The person who signs up for the Microsoft Entra tenant becomes a Global Administrator. |
| User Administrator |
|
|
| Billing Administrator |
|
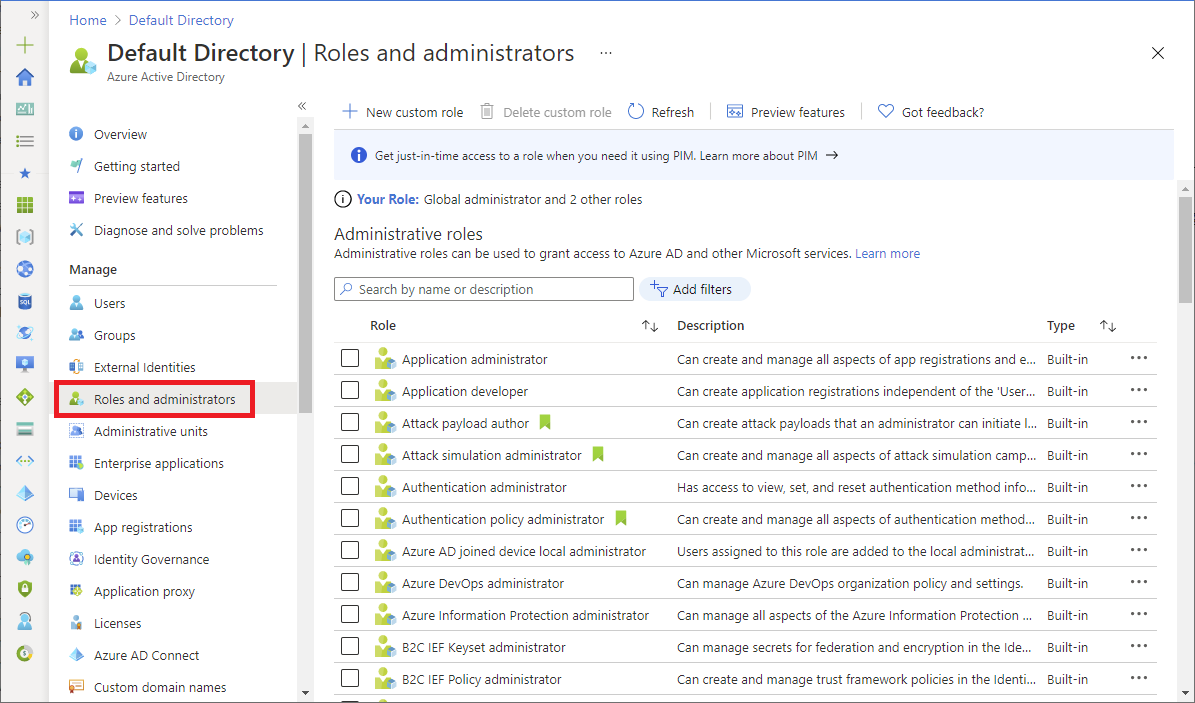
In the Azure portal, you can see the list of Microsoft Entra roles on the Roles and administrators page. For a list of all the Microsoft Entra roles, see Administrator role permissions in Microsoft Entra ID.
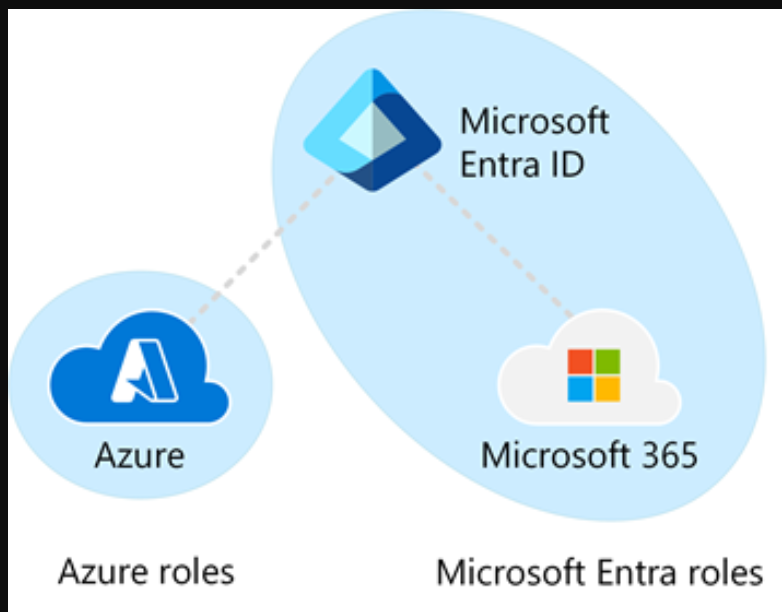
Differences between Azure roles and Microsoft Entra roles
At a high level, Azure roles control permissions to manage Azure resources, while Microsoft Entra roles control permissions to manage Microsoft Entra resources. The following table compares some of the differences.
| Azure roles | Microsoft Entra roles |
|---|---|
| Manage access to Azure resources | Manage access to Microsoft Entra resources |
| Supports custom roles | Supports custom roles |
| Scope can be specified at multiple levels (management group, subscription, resource group, resource) | Scope can be specified at the tenant level (organization-wide), administrative unit, or on an individual object (for example, a specific application) |
| Role information can be accessed in Azure portal, Azure CLI, Azure PowerShell, Azure Resource Manager templates, REST API | Role information can be accessed in the Azure portal, Microsoft Entra admin center, Microsoft 365 admin center, Microsoft Graph, Microsoft Graph PowerShell |
Do Azure roles and Microsoft Entra roles overlap?
By default, Azure roles and Microsoft Entra roles don't span Azure and Microsoft Entra ID. However, if a Global Administrator elevates their access by choosing the Access management for Azure resources switch in the Azure portal, the Global Administrator will be granted the User Access Administrator role (an Azure role) on all subscriptions for a particular tenant. The User Access Administrator role enables the user to grant other users access to Azure resources. This switch can be helpful to regain access to a subscription. For more information, see Elevate access to manage all Azure subscriptions and management groups.
Several Microsoft Entra roles span Microsoft Entra ID and Microsoft 365, such as the Global Administrator and User Administrator roles. For example, if you're a member of the Global Administrator role, you have global administrator capabilities in Microsoft Entra ID and Microsoft 365, such as making changes to Microsoft Exchange and Microsoft SharePoint. However, by default, the Global Administrator doesn't have access to Azure resources.
Classic subscription administrator roles
Important
Classic resources and classic administrators will be retired on August 31, 2024. Starting April 3, 2024, you won't be able to add new Co-Administrators. This date was recently extended. Remove unnecessary Co-Administrators and use Azure RBAC for fine-grained access control.
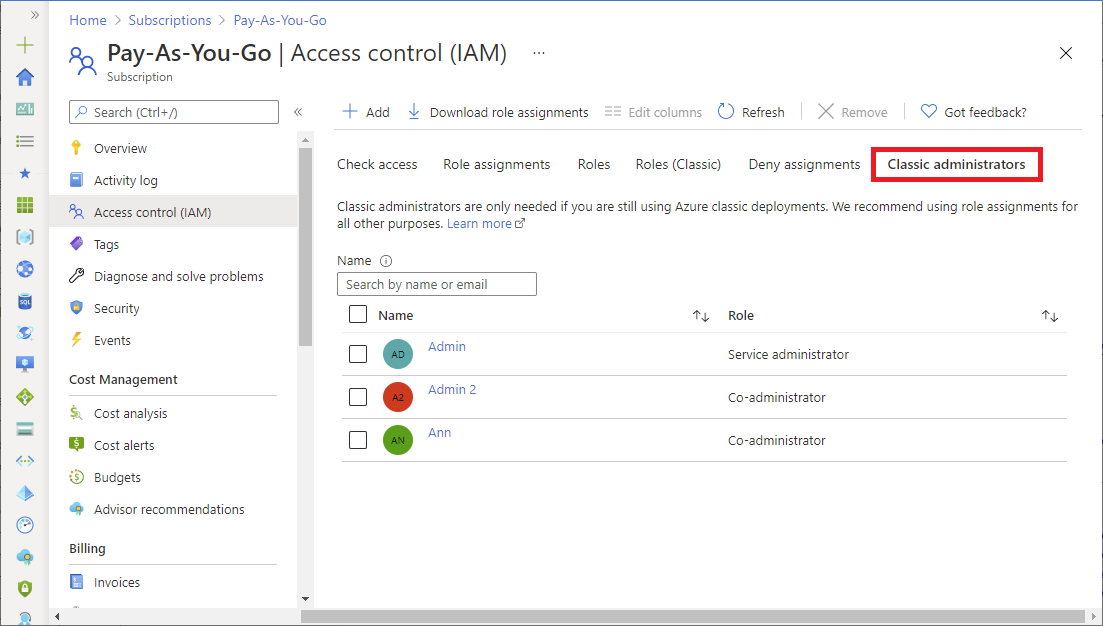
Account Administrator, Service Administrator, and Co-Administrator are the three classic subscription administrator roles in Azure. Classic subscription administrators have full access to the Azure subscription. They can manage resources using the Azure portal, Azure Resource Manager APIs, and the classic deployment model APIs. The account that is used to sign up for Azure is automatically set as both the Account Administrator and Service Administrator. Then, additional Co-Administrators can be added. The Service Administrator and the Co-Administrators have the equivalent access of users who have been assigned the Owner role (an Azure role) at the subscription scope. The following table describes the differences between these three classic subscription administrative roles.
| Classic subscription administrator | Limit | Permissions | Notes |
|---|---|---|---|
| Account Administrator | 1 per Azure account |
|
Conceptually, the billing owner of the subscription. |
| Service Administrator | 1 per Azure subscription |
|
By default, for a new subscription, the Account Administrator is also the Service Administrator. The Service Administrator has the equivalent access of a user who is assigned the Owner role at the subscription scope. The Service Administrator has full access to the Azure portal. |
| Co-Administrator | 200 per subscription |
|
The Co-Administrator has the equivalent access of a user who is assigned the Owner role at the subscription scope. |
In the Azure portal, you can manage Co-Administrators or view the Service Administrator by using the Classic administrators tab.
For more information, see Azure classic subscription administrators.
Azure account and Azure subscriptions
Azure帐户用于建立计费关系。Azure帐户是一个用户标识、一个或多个Azure订阅和一组关联的Azure资源。创建帐户的人是该帐户中创建的所有订阅的帐户管理员。此人也是订阅的默认服务管理员。
Azure订阅可帮助您组织对Azure资源的访问。它们还可以帮助您控制资源使用情况的报告、计费和支付方式。每个订阅可以有不同的计费和支付设置,因此您可以按办公室、部门、项目等有不同的订阅和不同的计划。大多数服务属于一个订阅,编程操作可能需要订阅ID。
每个订阅都与Microsoft Entra目录相关联。若要查找与订阅关联的目录,请在Azure门户中打开“订阅”,然后选择一个订阅以查看该目录。
帐户和订阅在Azure门户中管理。
Next steps
- 登录 发表评论
- 26 次浏览
最新内容
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago