category
Azure虚拟网络为构建高级网络架构提供了灵活的基础。使用各种类型的过滤组件(如Azure防火墙或您最喜欢的网络虚拟设备(NVA))管理异构环境需要一点规划。
Azure Bastion目前处于预览阶段,是一个完全托管的平台即服务(PaaS),它直接通过Azure门户提供对虚拟机(VM)的安全无缝的远程桌面协议(RDP)和安全shell(SSH)访问。Azure Bastion直接在您的虚拟网络中配置,支持所有连接的VM,而不会通过公共IP地址暴露。
当您部署Azure防火墙或任何NVAs时,您总是强制从子网隧道传输所有流量。应用0.0.0.0/0用户定义的路由可能会导致虚拟网络中工作负载的入口和出口流量的不对称路由。
虽然并非微不足道,但您经常发现自己需要为所有应用程序创建和管理一组不断增长的网络规则,包括DS NAT、转发等,以解决此问题。虽然这可能会影响您的所有应用程序,但RDP和SSH是最常见的示例。在这种情况下,来自互联网的入口流量可能会直接到达虚拟网络中的虚拟机,但出口流量最终会到达NVA。由于大多数NVAs都是有状态的,因此它最终会丢弃此流量,因为它最初没有收到它。
Azure Bastion允许在包含有状态的NVAs或启用了强制隧道的Azure防火墙的虚拟网络中为您的工作负载简化RDP/SSH设置。在本博客中,我们将探讨如何使其无缝工作。
- For a reference on how to deploy Azure Bastion (preview) in your virtual network, please see the documentation “Create an Azure Bastion host (Preview).”
- To learn how to implement Azure Firewall in your virtual network, refer to the documentation “Deploy and configure Azure Firewall using the Azure portal.”
Having deployed both Azure Bastion and Azure Firewall in your virtual network, let us look at how you can configure Azure Bastion to work in this scenario.
Configuring Azure Bastion
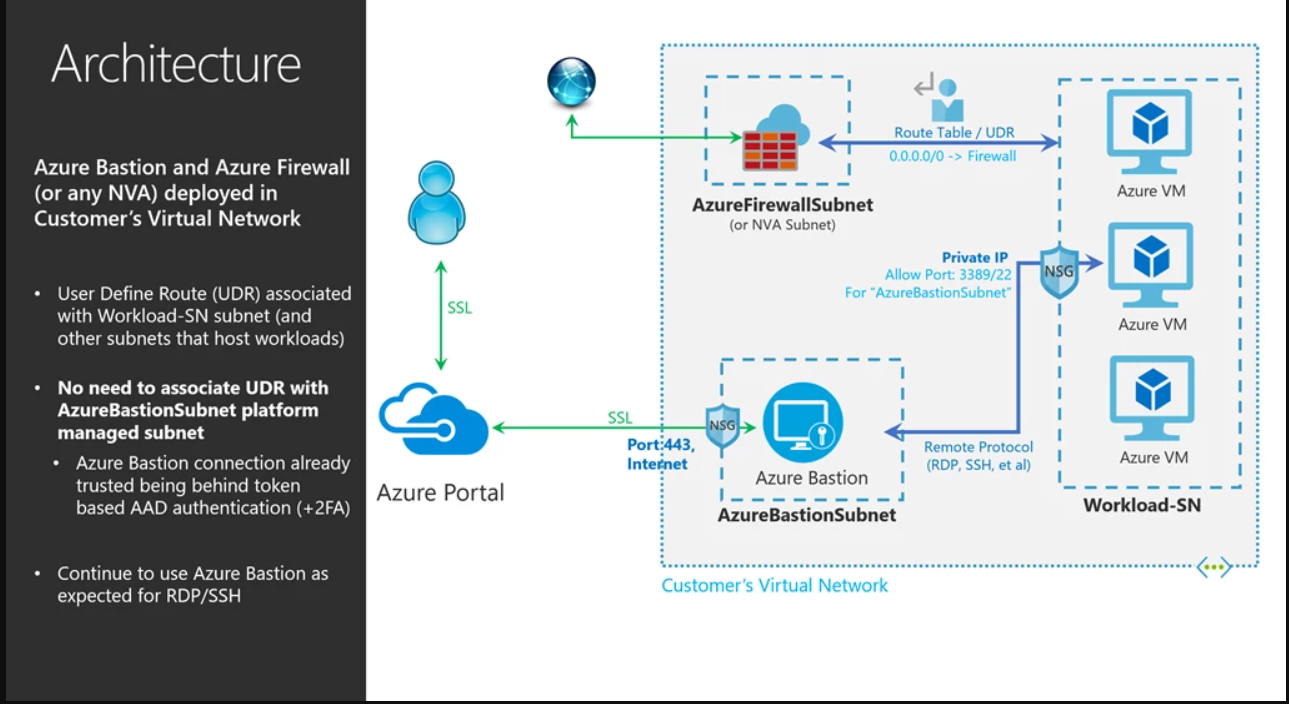
When deploying Azure Firewall, or a virtual appliance, you may end up associating your RouteTable, which was created while deploying Azure Firewall, to all subnets in your virtual network. You may even be including the AzureBastionSubnet subnet as well.
This applies a user-defined route to the AzureBastionSubnet subnet which directs all Azure Bastion traffic to Azure Firewall, thereby blocking traffic required for Azure Bastion. To avoid this, configuring Azure Bastion is very easy, but do not associate the RouteTable to AzureBastionSubnet subnet.
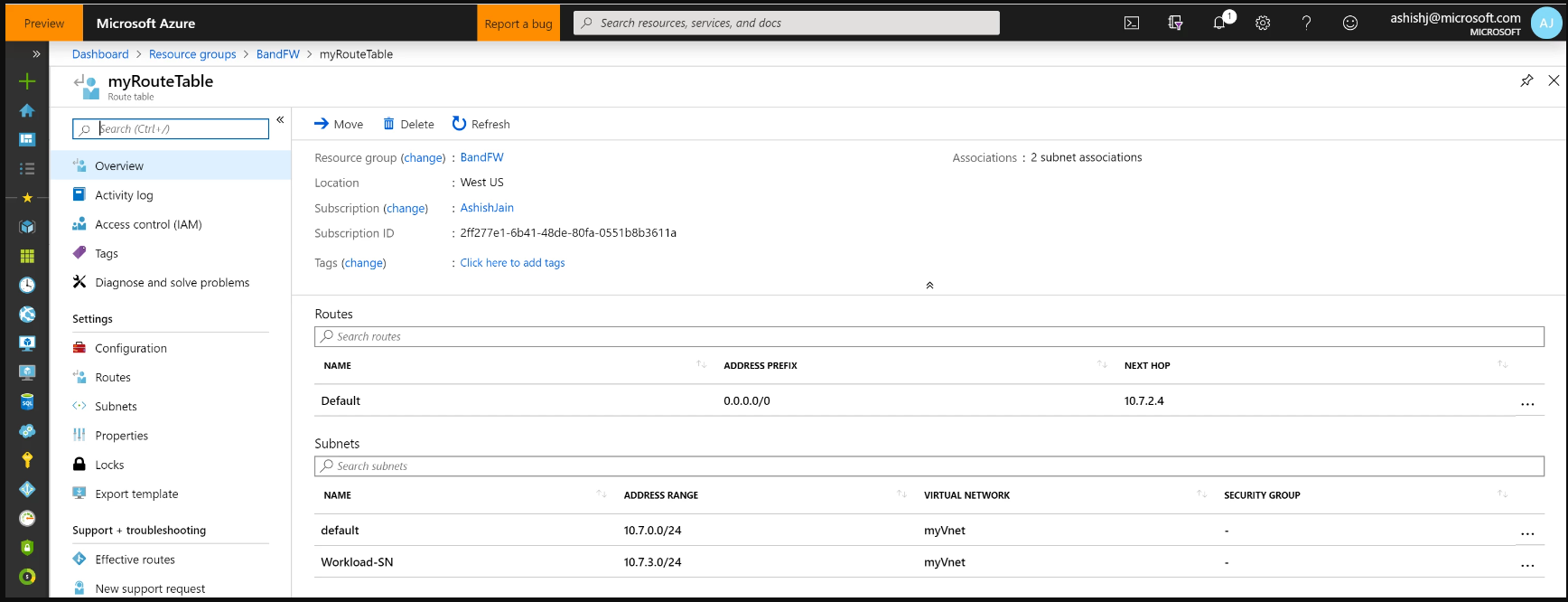
正如您在上面所注意到的,myRouteTable与AzureBastionSubnet不关联,而是与其他子网(如Workload SN)关联。
AzureBastionSubnet子网是安全的平台管理子网,除了Azure Bastion之外,其他Azure资源都不能部署在此子网中。所有与Azure Bastion的连接都是通过基于Azure Active Directory令牌的2FA身份验证强制执行的,所有流量都是加密的/通过HTTPS。
Azure Bastion经过内部加固,只允许通过端口443进行通信,从而省去了将其他网络安全组(NSG)或用户定义的路由应用于子网的任务。
这样,RDP/SSH请求将落在Azure Bastion上。使用上面的示例配置,默认路由(0.0.0.0/0)不适用于AzureBastionSubnet,因为它与此子网不关联。根据传入的RDP/SSH请求,Azure Bastion会连接到其他子网中的虚拟机,如工作负载SN,这些子网确实有默认路由关联。来自虚拟机的返回流量将直接到达您的虚拟网络中的Azure Bastion,而不是去往NVA-,因为返回流量被定向到虚拟网络中特定的私有IP。虚拟网络中具体的私有IP地址使其成为更具体的路由,因此优先于到NVA-的强制隧道路由,使您的RDP/SSH流量在虚拟网络中部署了NVA-或Azure防火墙时与Azure Bastion无缝协作。
我们非常感谢和赞赏客户和社区的参与和兴奋,并期待您的反馈,以进一步改进服务并使其尽快投入使用。
- 登录 发表评论
- 23 次浏览
最新内容
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago