category
This article describes how a cloud-based security information and event management (SIEM) solution like Microsoft Sentinel can use threat indicators to detect, provide context, and inform responses to existing or potential cyber threats.
Architecture
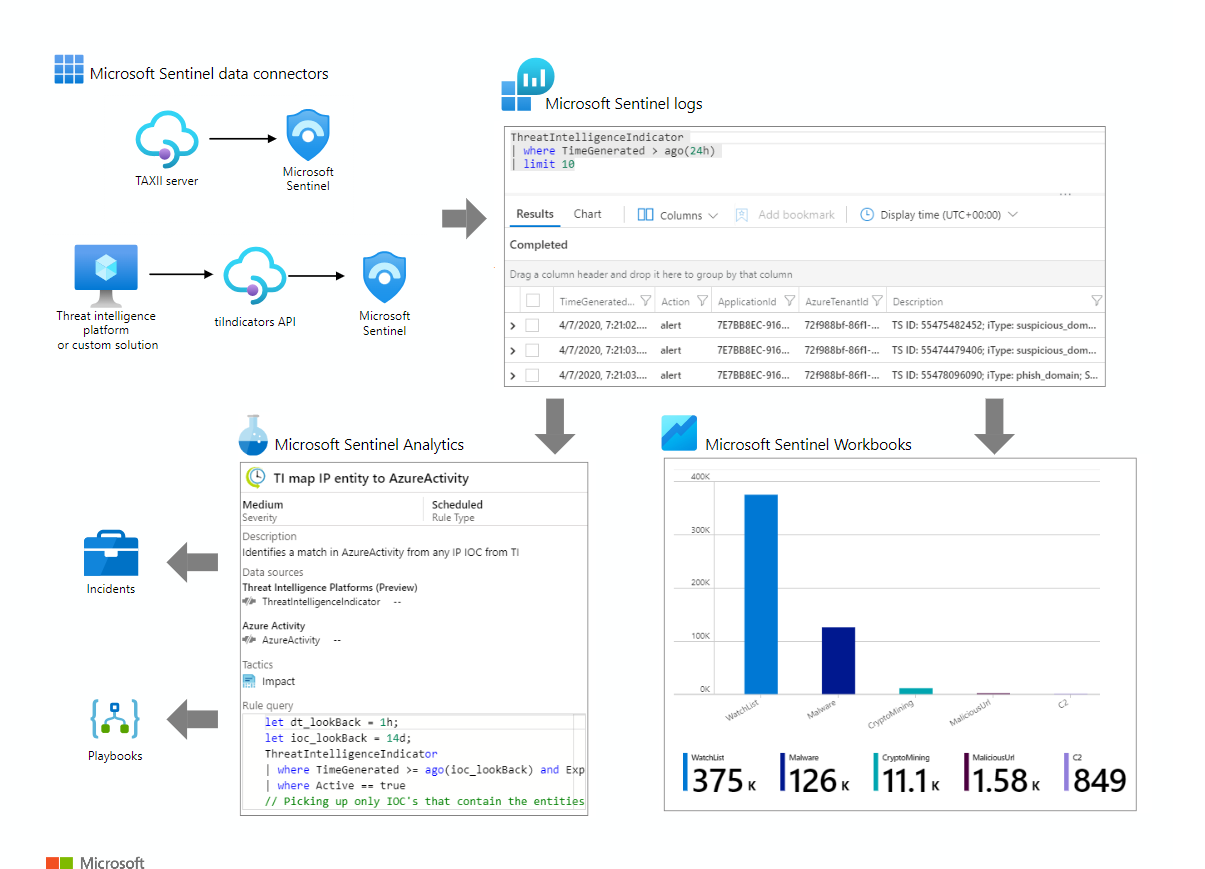
Download a Visio file of this architecture.
Workflow
You can use Microsoft Sentinel to:
- Import threat indicators from Structured Threat Information Expression (STIX) and Trusted Automated Exchange of Intelligence Information (TAXII) servers, or any threat intelligence platform (TIP) solution.
- View and query threat indicator data.
- Create analytics rules to generate security alerts, incidents, and automated responses from cyber threat intelligence (CTI) data.
- Visualize key CTI information in workbooks.
Threat indicator data connectors
Microsoft Sentinel imports threat indicators, like all other event data, by using data connectors. The two Microsoft Sentinel data connectors for threat indicators are:
- Threat Intelligence – TAXII
- Threat Intelligence Platforms
Depending on where your organization gets its threat indicator data, you can use either or both data connectors. Enable the data connectors in each workspace where you want to receive the data.
Threat Intelligence – TAXII data connector
The most widely adopted industry standard for CTI transmission is the STIX data format and TAXII protocol. Organizations that get threat indicators from current STIX/TAXII version 2.x solutions can import their threat indicators into Microsoft Sentinel by using the Threat Intelligence – TAXII data connector. The built-in Microsoft Sentinel TAXII client imports threat intelligence from TAXII 2.x servers.
For more information on how to import STIX/TAXII threat indicator data into Microsoft Sentinel, see Import threat indicators with the TAXII data connector.
Threat Intelligence Platforms data connector
Many organizations use TIP solutions like MISP, Anomali ThreatStream, ThreatConnect, or Palo Alto Networks MineMeld to aggregate threat indicator feeds from various sources. Organizations use the TIP to curate the data. Then they choose which threat indicators to apply to security solutions like network devices, advanced threat protection solutions, or SIEMs like Microsoft Sentinel. The Threat Intelligence Platforms data connector lets organizations use their integrated TIP solution with Microsoft Sentinel.
The Threat Intelligence Platforms data connector uses the Microsoft Graph Security tiIndicators API. Any organization that has a custom TIP can use this data connector to use the tiIndicators API and send indicators to Microsoft Sentinel and other Microsoft security solutions like Defender ATP.
For more information on how to import TIP data into Microsoft Sentinel, see Import threat indicators with the Platforms data connector.
Threat indicator logs
After you import threat indicators into Microsoft Sentinel by using the Threat Intelligence – TAXII or Threat Intelligence Platforms data connectors, you can view the imported data in the ThreatIntelligenceIndicator table in Logs, where all Microsoft Sentinel event data is stored. Microsoft Sentinel features like Analytics and Workbooks also use this table.
For more information on how to work with the threat indicators log, see Work with threat indicators in Microsoft Sentinel.
Microsoft Sentinel Analytics
The most crucial use for threat indicators in SIEM solutions is to power analytics that match events with threat indicators to produce security alerts, incidents, and automated responses. Microsoft Sentinel Analytics creates analytics rules that trigger on schedule to generate alerts. You express rule parameters as queries. Then you configure how often the rule runs, what query results generate security alerts and incidents, and any automated responses to the alerts.
You can create new analytics rules from scratch or a set of built-in Microsoft Sentinel rule templates that you can use or modify to meet your needs. The analytics rule templates that match threat indicators with event data are all titled starting with TI map. They all work similarly.
The template differences are which type of threat indicators to use, such as domain, email, file hash, IP address, or URL, and which event types to match against. Each template lists the required data sources for the rule to function, so you can see if you have the necessary events already imported in Microsoft Sentinel.
For more information on how to create an analytics rule from a template, see Create an analytics rule from a template.
In Microsoft Sentinel, enabled analytics rules are on the Active rules tab of the Analytics section. You can edit, enable, disable, duplicate, or delete active rules.
Generated security alerts are in the SecurityAlert table in the Logs section of Microsoft Sentinel. The security alerts also generate security incidents in the Incidents section. Security operations teams can triage and investigate the incidents to determine appropriate responses. For more information, see Tutorial: Investigate incidents with Microsoft Sentinel.
You can also designate automation to trigger when the rules generate security alerts. Automation in Microsoft Sentinel uses playbooks powered by Azure Logic Apps. For more information, see Tutorial: Set up automated threat responses in Microsoft Sentinel.
Microsoft Sentinel Threat Intelligence Workbook
Workbooks provide powerful interactive dashboards that give you insights into all aspects of Microsoft Sentinel. You can use a Microsoft Sentinel workbook to visualize key CTI information. The templates provide a starting point, and you can easily customize them for your business needs. You can create new dashboards that combine many different data sources and visualize your data in unique ways. Microsoft Sentinel workbooks are based on Azure Monitor workbooks, so extensive documentation and templates are available.
For more information on how to view and edit the Microsoft Sentinel Threat Intelligence Workbook, see View and edit the Threat Intelligence Workbook.
Alternatives
- Threat indicators provide useful context in other Microsoft Sentinel experiences like hunting and notebooks. For more information about using CTI in notebooks, see Jupyter notebooks in Sentinel.
- Any organization that has a custom TIP can use the Microsoft Graph Security tiIndicators API to send threat indicators to other Microsoft security solutions like Defender ATP.
- Microsoft Sentinel provides many other built-in data connectors to solutions like Microsoft Threat Protection, Microsoft 365 sources, and Microsoft Defender for Cloud Apps. There are also built-in connectors to the broader security ecosystem for non-Microsoft solutions. You can also use common event format, Syslog, or REST API to connect your data sources with Microsoft Sentinel. For more information, see Connect data sources.
Scenario details
Cyber threat intelligence can come from many sources, such as open-source data feeds, threat intelligence sharing communities, paid intelligence feeds, and security investigations within organizations.
CTI can range from written reports on a threat actor's motivations, infrastructure, and techniques to specific observations of IP addresses, domains, and file hashes. CTI provides essential context for unusual activity, so security personnel can act quickly to protect people and assets.
The most utilized CTI in SIEM solutions like Microsoft Sentinel is threat indicator data, sometimes called Indicators of Compromise (IoCs). Threat indicators associate URLs, file hashes, IP addresses, and other data with known threat activity like phishing, botnets, or malware.
This form of threat intelligence is often called tactical threat intelligence because security products and automation can use it on a large scale to protect and detect potential threats. Microsoft Sentinel can help detect, respond to, and provide CTI context for malicious cyber activity.
Potential use cases
- Connect to open-source threat indicator data from public servers to identify, analyze, and respond to threat activity.
- Use existing threat intelligence platforms or custom solutions with the Microsoft Graph
tiIndicatorsAPI to connect and control access to threat indicator data. - Provide CTI context and reporting for security investigators and stakeholders.
Considerations
- The Microsoft Sentinel Threat Intelligence data connectors are currently in public preview. Certain features might not be supported or might have constrained capabilities.
- Microsoft Sentinel uses Azure role-based access control (Azure RBAC) to assign the built-in roles Contributor, Reader, and Responder to users, groups, and Azure services. These roles can interact with Azure roles (Owner, Contributor, Reader) and Log Analytics roles (Log Analytics reader, Log Analytics contributor). You can create custom roles and use advanced Azure RBAC on the data you store in Microsoft Sentinel. For more information, see Permissions in Microsoft Sentinel.
- Microsoft Sentinel is free for the first 31 days on any Azure Monitor Log Analytics workspace. Afterward, you can use pay-as-you-go or Capacity Reservations models for the data you ingest and store. For more information, see Microsoft Sentinel pricing.
Deploy this scenario
The following sections provide steps on how to:
- Enable the Threat Intelligence – TAXII and Threat Intelligence Platforms data connectors.
- Create an example Microsoft Sentinel Analytics rule to generate security alerts and incidents from CTI data.
- View and edit the Microsoft Sentinel Threat Intelligence Workbook.
Import threat indicators with the TAXII data connector
Warning
The following instructions use Limo, Anomali's free STIX/TAXII feed. This feed has reached end-of-life and is no longer being updated. The following instructions can't be completed as written. You can substitute this feed with another API-compatible feed you can access.
TAXII 2.x servers advertise API roots, which are URLs that host threat intelligence collections. If you already know the TAXII server API root and Collection ID you want to work with, you can skip ahead and enable the TAXII connector in Microsoft Sentinel.
If you don't have the API root, you can usually get it from the threat intelligence provider's documentation page, but sometimes the only information available is the discovery endpoint URL. You can find the API root by using the discovery endpoint. The following example uses the discovery endpoint of the Anomali Limo ThreatStream TAXII 2.0 server.
-
From a browser, go to the ThreatStream TAXII 2.0 server discovery endpoint,
https://limo.anomali.com/taxii. Sign in by using the username guest and password guest. After you sign in, you see the following information:JSON{ "api_roots": [ "https://limo.anomali.com/api/v1/taxii2/feeds/", "https://limo.anomali.com/api/v1/taxii2/trusted_circles/", "https://limo.anomali.com/api/v1/taxii2/search_filters/" ], "contact": "info@anomali.com", "default": "https://limo.anomali.com/api/v1/taxii2/feeds/", "description": "TAXII 2.0 Server (guest)", "title": "ThreatStream Taxii 2.0 Server" } -
To browse collections, enter the API root you got from the previous step into your browser:
https://limo.anomali.com/api/v1/taxii2/feeds/collections/. You see information like:JSON{ "collections": [ { "can_read": true, "can_write": false, "description": "", "id": "107", "title": "Phish Tank" }, ... { "can_read": true, "can_write": false, "description": "", "id": "41", "title": "CyberCrime" } ] }
You now have the information you need to connect Microsoft Sentinel to one or more TAXII server collections provided by Anomali Limo. For example:
| API root | Collection ID |
|---|---|
| Phish Tank | 107 |
| CyberCrime | 41 |
To enable the Threat Intelligence – TAXII data connector in Microsoft Sentinel:
-
In the Azure portal, search for and select Microsoft Sentinel.
-
Select the workspace where you want to import threat indicators from the TAXII service.
-
Select Data connectors from the leftmost pane. Search for and select Threat Intelligence – TAXII (Preview) and select Open connector page.
-
On the Configuration page, enter a Friendly name (for server) value such as the collection title. Enter the API root URL and Collection ID you want to import. Enter a username and password if required, and select Add.
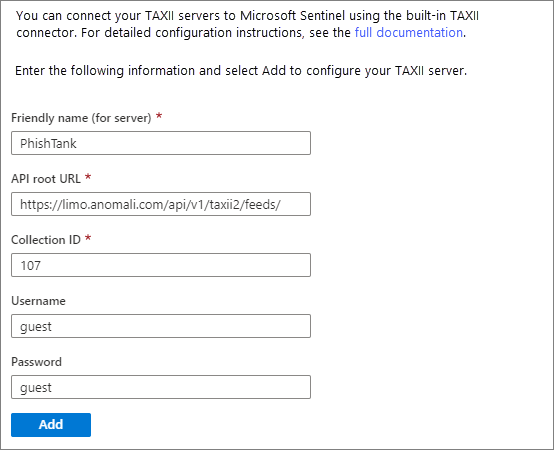
You see your connection under a list of configured TAXII 2.0 servers. Repeat the configuration for each collection you want to connect from the same or different TAXII servers.
Import threat indicators with the Platforms data connector
The tiIndicators API needs the Application (client) ID, Directory (tenant) ID, and client secret from your TIP or custom solution to connect and send threat indicators to Microsoft Sentinel. To get this information, register the TIP or solution app in Microsoft Entra ID and grant it the needed permissions.
For more information, see Connect your threat intelligence platform to Microsoft Sentinel.
Create an Analytics rule from a template
This example uses the rule template called TI map IP entity to AzureActivity, which compares any IP address-type threat indicators with all your Azure Activity IP address events. Any match generates a security alert and a corresponding incident for investigation by your security operations team.
The example assumes you've used one or both threat intelligence data connectors to import threat indicators and the Azure Activity data connector to import your Azure subscription-level events. You need both data types to use this analytics rule successfully.
-
In the Azure portal, search for and select Microsoft Sentinel.
-
Select the workspace where you imported threat indicators with either threat intelligence data connector.
-
On the leftmost pane, select Analytics.
-
On the Rule templates tab, search for and select the rule (Preview) TI map IP entity to AzureActivity. Select Create rule.
-
On the first Analytic rule wizard - Create new rule from template page, make sure the rule Status is set to Enabled. Change the rule name or description if you want. Select Next: Set rule logic.
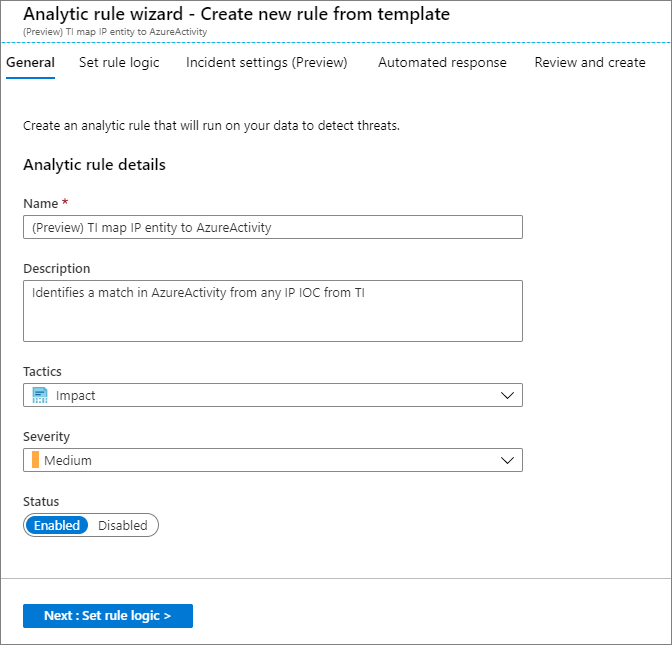
The rule logic page contains the query for the rule, entities to map, rule scheduling, and the number of query results that generate a security alert. The template settings run once an hour. They identify any IP address IoCs that match any IP addresses from Azure events. They also generate security alerts for all matches. You can keep these settings or change any of them to meet your needs. When you're finished, select Next: Incident settings (Preview).
-
Under Incident settings (Preview), make sure that Create incidents from alerts triggered by this analytics rule is set to Enabled. Select Next: Automated response.
This step lets you configure automation to trigger when the rule generates a security alert. Automation in Microsoft Sentinel uses playbooks powered by Azure Logic Apps. For more information, see Tutorial: Set up automated threat responses in Microsoft Sentinel. For this example, select Next: Review. After you review the settings, select Create.
Your rule activates immediately when it's created and then triggers on the regular schedule.
View and edit the Threat Intelligence Workbook
-
In the Azure portal, search for and select Microsoft Sentinel.
-
Select the workspace where you've imported threat indicators with either threat intelligence data connector.
-
On the leftmost pane, select Workbooks.
-
Search for and select the workbook titled Threat Intelligence.
-
Make sure you have the necessary data and connections as shown. Select Save.
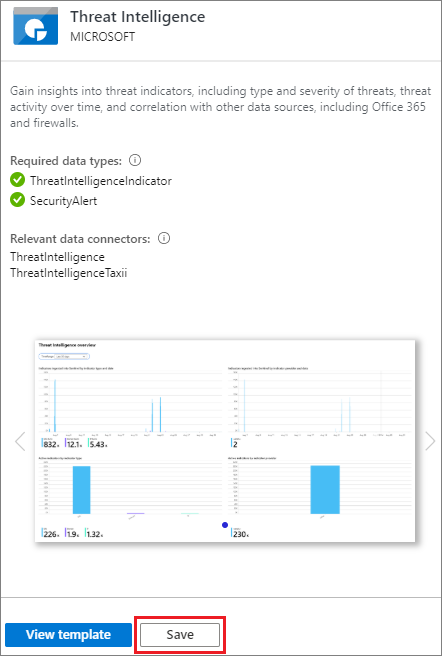
In the pop-up window, select a location and then select OK. This step saves the workbook so that you can modify it and save your changes.
-
Select View saved workbook to open the workbook and see the default charts the template provides.
To edit the workbook, select Edit. You can select Edit next to any chart to edit the query and settings for that chart.
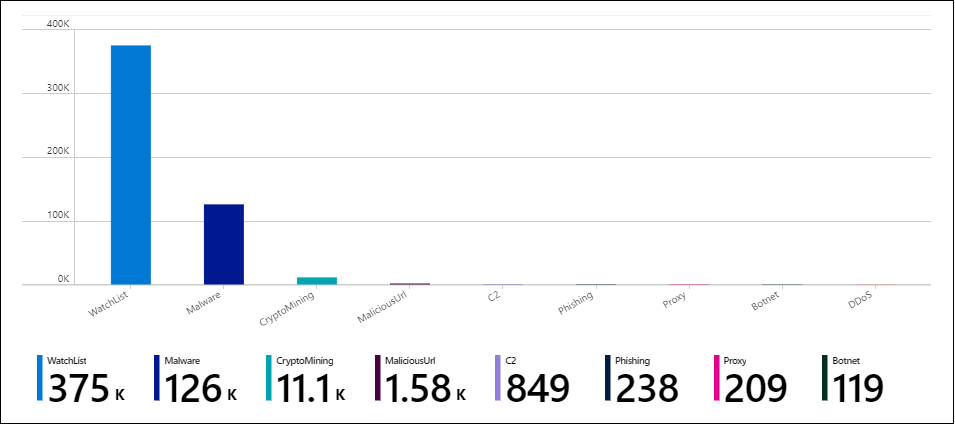
To add a new chart that shows threat indicators by threat type:
-
Select Edit. Scroll to the bottom of the page and select Add > Add query.
-
Under Log Analytics workspace Logs Query, enter the following query:
ThreatIntelligenceIndicator | summarize count() by ThreatType -
Select Bar chart in the Visualization dropdown and select Done editing.
-
At the top of the page, select Done editing. Select the Save icon to save your new chart and workbook.
Next steps
Go to the Microsoft Sentinel repo on GitHub to see contributions by the community at large and by Microsoft. Here you find new ideas, templates, and conversations about all the feature areas of Microsoft Sentinel.
Microsoft Sentinel workbooks are based on Azure Monitor workbooks, so extensive documentation and templates are available. A great place to start is Create interactive reports with Azure Monitor workbooks. There's collection of community driven Azure Monitor Workbook Templates on GitHub to download.
To learn more about the featured technologies, see:
- What is Microsoft Sentinel?
- Quickstart: On-board Microsoft Sentinel
- Microsoft Graph Security tiIndicators API
- Tutorial: Investigate incidents with Microsoft Sentinel
- Tutorial: Set up automated threat responses in Microsoft Sentinel
Related resources
- 登录 发表评论
- 30 次浏览
最新内容
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago