category
Application Gateway Private Link允许您通过跨越VNet和订阅的专用连接来连接工作负载。有关更多信息,请参阅应用程序网关专用链接。
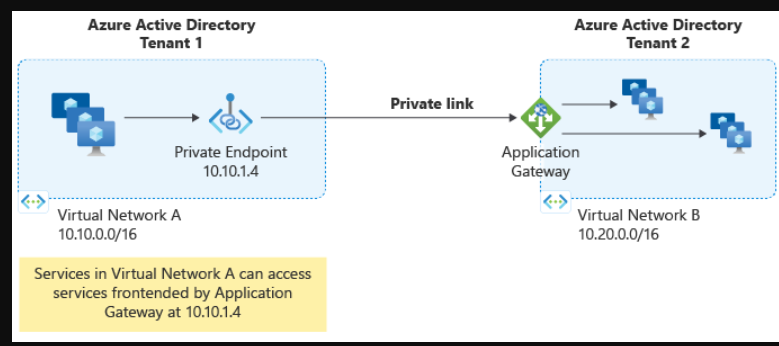
应用程序网关专用链接示意图
配置选项
应用程序网关专用链接可以通过多种选项进行配置,例如但不限于Azure门户、Azure PowerShell和Azure CLI。
Azure门户
定义专用链路配置的子网
要启用专用链路配置,专用链路IP配置需要不同于应用程序网关子网的子网。专用链接必须使用不包含任何应用程序网关的子网。子网大小由部署所需的连接数决定。分配给该子网的每个IP地址确保64-K并发TCP连接,这些连接可以在单个时间点通过专用链路建立。分配更多的IP地址以允许通过专用链接进行更多的连接。例如:n*64K;其中n是被提供的IP地址的数目。
笔记
每个专用链路配置的最大IP地址数为八个。仅支持动态分配。
完成以下步骤以创建新子网:
添加、更改或删除虚拟网络子网
配置专用链接
专用链路配置定义应用程序网关用于启用来自专用端点的连接的基础结构。在创建专用链路配置时,请确保侦听器正在积极利用受尊重的前端IP配置。完成以下步骤以创建专用链接配置:
- 转到Azure门户
- 搜索并选择“应用程序网关”。
- 选择要启用专用链接的应用程序网关的名称。
- 选择专用链接
- 配置以下项目:
- 名称:专用链接配置的名称。
- 专用链接子网:应从使用子网IP地址。
- 前端IP配置:专用链路应在应用程序网关上将流量转发到的前端IP地址。
- 专用IP地址设置:至少指定一个IP地址
- 选择添加。
- 在应用程序网关属性刀片中,获取并记录资源ID,如果要在不同的Microsoft Entra租户中设置专用端点,则需要这样做。
配置专用终结点
专用端点是一种网络接口,它使用来自包含希望连接到应用程序网关的客户端的虚拟网络的专用IP地址。每个客户端都使用专用端点的专用IP地址将流量隧道传输到应用程序网关。要创建专用终结点,请完成以下步骤:
- 选择专用端点连接选项卡。
- 选择“创建”。
- 在“基本”选项卡上,为专用端点配置资源组、名称和区域。选择“下一步”。
- 在“资源”选项卡上,选择“下一步”。
- 在“虚拟网络”选项卡上,配置专用端点网络接口应设置到的虚拟网络和子网。配置专用端点应具有动态IP地址还是静态IP地址。
- 择“下一步”。
- 在“标记”选项卡上,可以选择配置资源标记。选择“下一步”。
- 选择“创建”。
笔记如果在创建专用端点的“资源”选项卡上尝试选择目标子资源时缺少公共或专用IP配置资源,请确保侦听器正在积极使用受尊重的前端IP配置。没有关联侦听器的前端IP配置将不会显示为目标子资源。
笔记
如果您正在从另一个租户内配置专用端点,则需要使用Azure应用程序网关资源ID和前端IP配置的名称作为目标子资源。例如,如果我有一个与应用程序网关关联的专用IP,并且该专用IP在门户的前端IP配置中列出的名称为PrivateFrontendIp,则目标子资源值将为:PrivateFrontendIp。
笔记
如果必须将专用端点移动到另一个订阅,则必须首先删除专用链接和专用端点之间的现有专用端点连接。完成后,您必须在新订阅中重新创建一个新的专用端点连接,以在专用链接和专用端点之间建立连接。
Azure PowerShell
To configure Private link on an existing Application Gateway via Azure PowerShell, use following commands:
# Disable Private Link Service Network Policies
# https://learn.microsoft.com/azure/private-link/disable-private-endpoint-network-policy
$net =@{
Name = 'AppGW-PL-PSH'
ResourceGroupName = 'AppGW-PL-PSH-RG'
}
$vnet = Get-AzVirtualNetwork @net
($vnet | Select -ExpandProperty subnets | Where-Object {$_.Name -eq 'AppGW-PL-Subnet'}).PrivateLinkServiceNetworkPolicies = "Disabled"
$vnet | Set-AzVirtualNetwork
# Get Application Gateway Frontend IP Name
$agw = Get-AzApplicationGateway -Name AppGW-PL-PSH -ResourceGroupName AppGW-PL-PSH-RG
# List the names
$agw.FrontendIPConfigurations | Select Name
# Add a new Private Link configuration and associate it with an existing Frontend IP
$PrivateLinkIpConfiguration = New-AzApplicationGatewayPrivateLinkIpConfiguration `
-Name "ipConfig01" `
-Subnet ($vnet | Select -ExpandProperty subnets
| Where-Object {$_.Name -eq 'AppGW-PL-Subnet'}) `
-Primary
# Add the Private Link configuration to the gateway configuration
Add-AzApplicationGatewayPrivateLinkConfiguration `
-ApplicationGateway $agw `
-Name "privateLinkConfig01" `
-IpConfiguration $PrivateLinkIpConfiguration
# Associate private link configuration to Frontend IP
$agwPip = ($agw | Select -ExpandProperty FrontendIpConfigurations|
Where-Object {$_.Name -eq 'appGwPublicFrontendIp'}).PublicIPAddress.Id
$privateLinkConfiguration = ($agw | Select -ExpandProperty PrivateLinkConfigurations |
Where-Object {$_.Name -eq 'privateLinkConfig01'}).Id
Set-AzApplicationGatewayFrontendIPConfig -ApplicationGateway $agw -Name "appGwPublicFrontendIp"
-PublicIPAddressId $agwPip -PrivateLinkConfigurationId $privateLinkConfiguration
# Apply the change to the gateway
Set-AzApplicationGateway -ApplicationGateway $agw
# Disable Private Endpoint Network Policies
# https://learn.microsoft.com/azure/private-link/disable-private-endpoint-network-policy
$net =@{
Name = 'AppGW-PL-Endpoint-PSH-VNET'
ResourceGroupName = 'AppGW-PL-Endpoint-PSH-RG'
}
$vnet_plendpoint = Get-AzVirtualNetwork @net
($vnet_plendpoint | Select -ExpandProperty subnets |
Where-Object {$_.Name -eq 'MySubnet'}).PrivateEndpointNetworkPolicies = "Disabled"
$vnet_plendpoint | Set-AzVirtualNetwork
# Create Private Link Endpoint - Group ID is the same as the frontend IP configuration
$privateEndpointConnection = New-AzPrivateLinkServiceConnection
-Name "AppGW-PL-Connection" -PrivateLinkServiceId $agw.Id -GroupID "appGwPublicFrontendIp"
## Create private endpoint
New-AzPrivateEndpoint -Name "AppGWPrivateEndpoint"
-ResourceGroupName $vnet_plendpoint.ResourceGroupName -Location $vnet_plendpoint.Location
-Subnet ($vnet_plendpoint | Select -ExpandProperty subnets | Where-Object {$_.Name -eq 'MySubnet'})
-PrivateLinkServiceConnection $privateEndpointConnection
The following is a list of all Azure PowerShell references for Private Link Configuration on Application Gateway:
- Get-AzApplicationGatewayPrivateLinkConfiguration
- New-AzApplicationGatewayPrivateLinkConfiguration
- New-AzApplicationGatewayPrivateLinkIpConfiguration
- Add-AzApplicationGatewayPrivateLinkConfiguration
- Remove-AzApplicationGatewayPrivateLinkConfiguration
- Set-AzApplicationGatewayPrivateLinkConfiguration
Azure CLI
To configure Private link on an existing Application Gateway via Azure CLI, use following commands:
# Disable Private Link Service Network Policies
# https://learn.microsoft.com/azure/private-link/disable-private-endpoint-network-policy
az network vnet subnet update \
--name AppGW-PL-Subnet \
--vnet-name AppGW-PL-CLI-VNET \
--resource-group AppGW-PL-CLI-RG \
--disable-private-link-service-network-policies true
# Get Application Gateway Frontend IP Name
az network application-gateway frontend-ip list \
--gateway-name AppGW-PL-CLI \
--resource-group AppGW-PL-CLI-RG
# Add a new Private Link configuration and associate it with an existing Frontend IP
az network application-gateway private-link add \
--frontend-ip appGwPublicFrontendIp \
--name privateLinkConfig01 \
--subnet /subscriptions/XXXXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXX/
resourceGroups/AppGW-PL-CLI-RG/providers/Microsoft.Network/virtualNetworks/
AppGW-PL-CLI-VNET/subnets/AppGW-PL-Subnet \
--gateway-name AppGW-PL-CLI \
--resource-group AppGW-PL-CLI-RG
# Get Private Link resource ID
az network application-gateway private-link list \
--gateway-name AppGW-PL-CLI \
--resource-group AppGW-PL-CLI-RG
# Disable Private Endpoint Network Policies
# https://learn.microsoft.com/azure/private-link/disable-private-endpoint-network-policy
az network vnet subnet update \
--name MySubnet \
--vnet-name AppGW-PL-Endpoint-CLI-VNET \
--resource-group AppGW-PL-Endpoint-CLI-RG \
--disable-private-endpoint-network-policies true
# Create Private Link Endpoint - Group ID is the same as the frontend IP configuration
az network private-endpoint create \
--name AppGWPrivateEndpoint \
--resource-group AppGW-PL-Endpoint-CLI-RG \
--vnet-name AppGW-PL-Endpoint-CLI-VNET \
--subnet MySubnet \
--group-id appGwPublicFrontendIp \
--private-connection-resource-id /subscriptions/XXXXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXX/
resourceGroups/AppGW-PL-CLI-RG/providers/Microsoft.Network/applicationGateways/AppGW-PL-CLI \
--connection-name AppGW-PL-Connection
A list of all Azure CLI references for Private Link Configuration on Application Gateway is available here: Azure CLI CLI - Private Link
接下来的步骤
- Learn about Azure Private Link: What is Azure Private Link.
- 登录 发表评论
- 31 次浏览
最新内容
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago