category
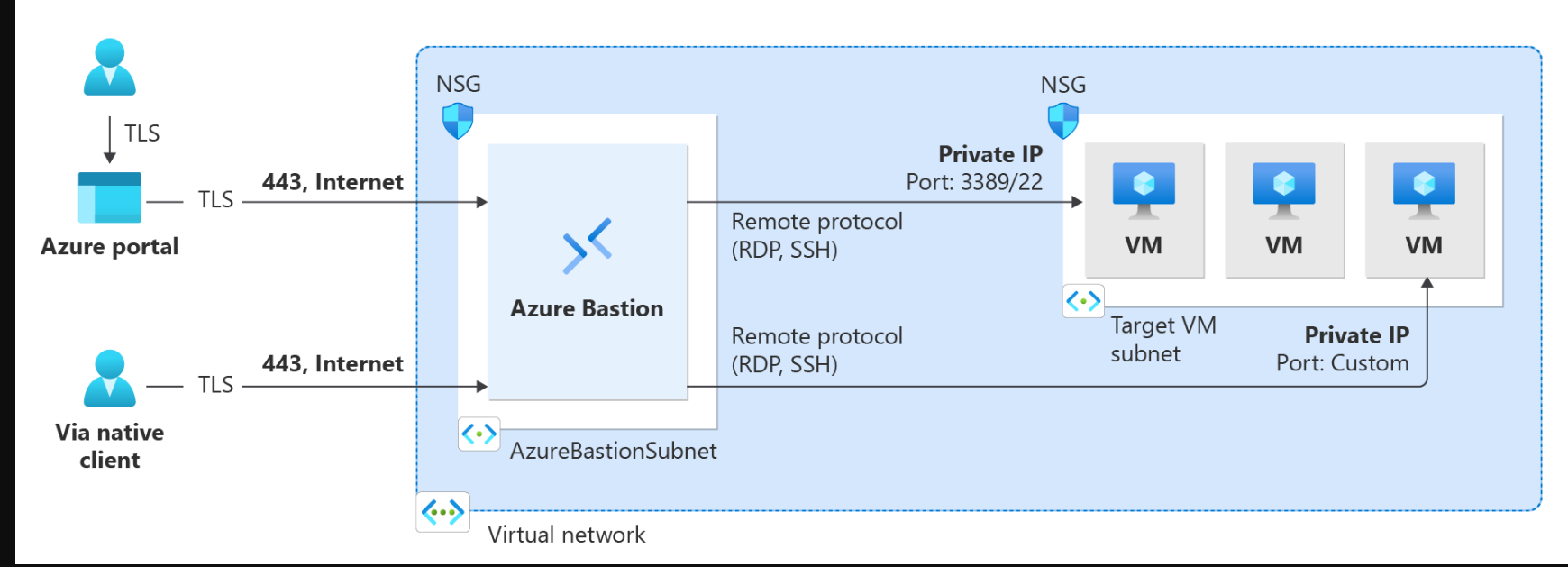
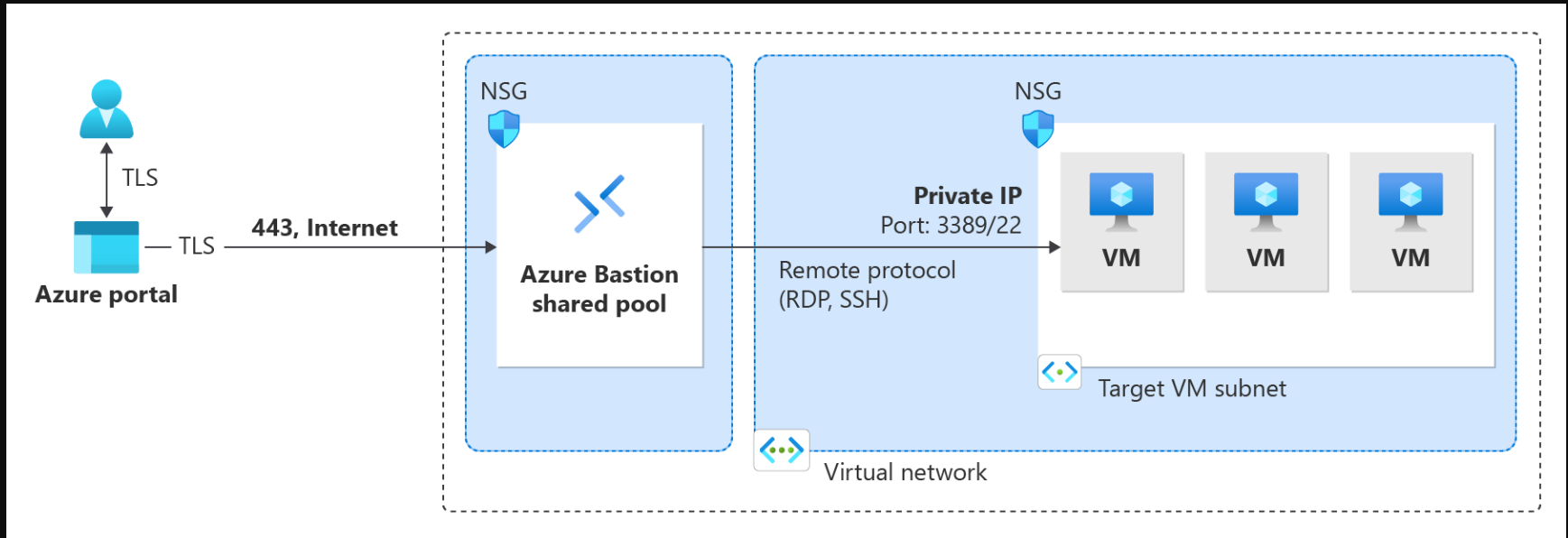
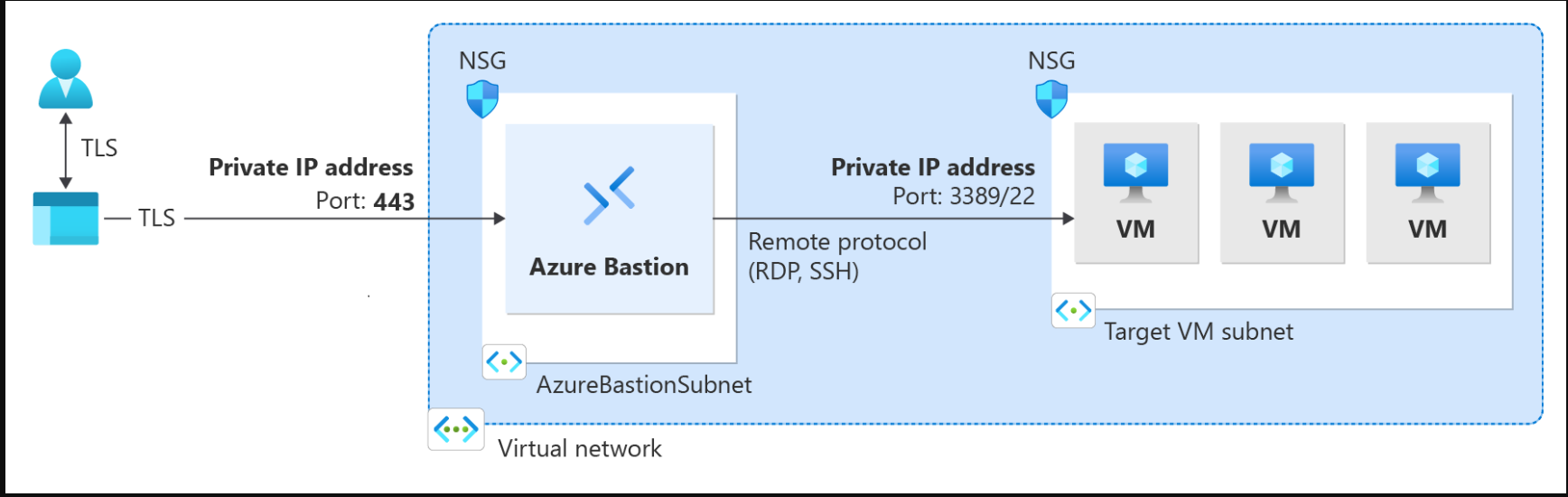
Azure Bastion提供多种部署架构,具体取决于所选的SKU和选项配置。对于大多数SKU,Bastion部署到虚拟网络并支持虚拟网络对等。具体来说,Azure Bastion管理与在本地或对等虚拟网络中创建的VM的RDP/SSH连接。 When working with the Basic SKU or higher, Bastion uses the following architecture and workflow. For some configurations, the user can connect to the virtual machine via the native operating system client. For configuration steps, see: The Bastion Developer SKU is a free, lightweight SKU. This SKU is ideal for Dev/Test users who want to securely connect to their VMs, but don't need additional Bastion features or host scaling. With the Developer SKU, you can connect to one Azure VM at a time directly through the virtual machine connect page. When you deploy Bastion using the Developer SKU, the deployment requirements are different than when you deploy using other SKUs. Typically when you create a bastion host, a host is deployed to the AzureBastionSubnet in your virtual network. The Bastion host is dedicated for your use. When you use the Developer SKU, a bastion host isn't deployed to your virtual network and you don't need an AzureBastionSubnet. However, the Developer SKU bastion host isn't a dedicated resource. Instead, it's part of a shared pool. Because the Developer SKU bastion resource isn't dedicated, the features for the Developer SKU are limited. See the Bastion configuration settings SKU section for features listed by SKU. You can always upgrade the Developer SKU to a higher SKU if you need to support more features. See Upgrade a SKU. For more information about the Developer SKU, see Deploy Azure Bastion - Developer SKU. Private-only Bastion deployments lock down workloads end-to-end by creating a non-internet routable deployment of Bastion that allows only private IP address access. Private-only Bastion deployments don't allow connections to the bastion host via public IP address. In contrast, a regular Azure Bastion deployment allows users to connect to the bastion host using a public IP address.. The diagram shows the Bastion private-only deployment architecture. A user connected to Azure via ExpressRoute private-peering can securely connect to Bastion using the private IP address of the bastion host. Bastion can then make the connection via private IP address to a virtual machine that's within the same virtual network as the bastion host. In a private-only Bastion deployment, Bastion doesn't allow outbound access outside of the virtual network. Considerations: Private-only Bastion is configured at the time of deployment and requires the Premium SKU Tier. You can't change from a regular Bastion deployment to a private-only deployment. To deploy private-only Bastion to a virtual network that already has a Bastion deployment, first remove Bastion from your virtual network, then deploy Bastion back to the virtual network as private-only. You don't need to delete and recreate the AzureBastionSubnet. If you want to create end-to-end private connectivity, connect using the native client instead of connecting via the Azure portal. If your client machine is on-premises and non-Azure, you will need to deploy an ExpressRoute or VPN and enable IP-based connection on the Bastion resource For more information about private-only deployments, see Deploy Bastion as private-only.
RDP和SSH是您可以连接到在Azure中运行的工作负载的一些基本手段。在互联网上暴露RDP/SSH端口是不可取的,被视为一个重大的威胁面。这通常是由于协议漏洞造成的。为了遏制这种威胁,您可以在外围网络的公共端部署堡垒主机(也称为跳转服务器)。堡垒主机服务器的设计和配置可以抵御攻击。Bastion服务器还为位于堡垒后面以及网络内部的工作负载提供RDP和SSH连接。
部署Bastion时选择的SKU决定了架构和可用功能。您可以升级到更高的SKU以支持更多功能,但部署后不能降级SKU。某些架构,如Private only和Developer SKU,必须在部署时进行配置。Deployment - Basic SKU and higher
Deployment - Developer SKU
Deployment - Private-only (Preview)
Next steps
- 登录 发表评论
- 25 次浏览
Tags
最新内容
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago
- 1 month 2 weeks ago