【SaaS架构】使用AWS Lambda令牌自动售货机为Amazon S3实施SaaS租户隔离
视频号
微信公众号
知识星球
多租户SaaS应用程序必须实现系统,以确保租户隔离得到维护。当您在同一Amazon Web Services(AWS)资源上存储租户数据时,例如多个租户在同一亚马逊简单存储服务(Amazon S3)存储桶中存储数据时,您必须确保不会发生跨租户访问。
Created by Tabby Ward (AWS), sravan periyathambi (AWS), and Thomas Davis (AWS)
|
Environment: PoC or pilot |
Technologies: Modernization; SaaS |
AWS services: AWS Identity and Access Management; AWS Lambda; Amazon S3; AWS STS |
总结
多租户SaaS应用程序必须实现系统,以确保租户隔离得到维护。当您在同一Amazon Web Services(AWS)资源上存储租户数据时,例如多个租户在同一亚马逊简单存储服务(Amazon S3)存储桶中存储数据时,您必须确保不会发生跨租户访问。令牌自动售货机(TVM)是保证租户数据隔离的一种方式。这些机器提供了一种获取令牌的机制,同时抽象了如何生成这些令牌的复杂性。开发人员可以使用TVM,而无需详细了解它如何生成令牌。
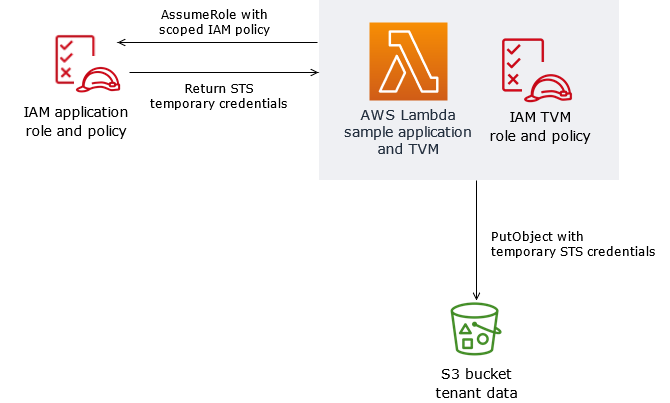
此模式通过使用AWS Lambda实现TVM。TVM生成一个令牌,该令牌由临时安全令牌服务(STS)凭证组成,这些凭证限制对S3存储桶中单个SaaS租户数据的访问。
TVM和随此模式提供的代码通常与从JSON Web令牌(JWT)派生的声明一起使用,以将AWS资源请求与租户范围的AWS身份和访问管理(IAM)策略相关联。您可以使用此模式中的代码作为实现SaaS应用程序的基础,该应用程序基于JWT令牌中提供的声明生成作用域的临时STS凭证。
先决条件和限制
先决条件
- 活跃的AWS帐户。
- AWS命令行界面(AWS CLI)1.19.0或更高版本,在macOS、Linux或Windows上安装和配置。或者,您可以使用AWS CLI 2.1版或更高版本。
局限性
- 此代码在Java中运行,目前不支持其他编程语言。
- 示例应用程序不包括AWS跨区域或灾难恢复(DR)支持。
- 此模式演示了SaaS应用程序的Lambda TVM如何提供范围内的租户访问。它不打算用于生产环境。
架构
目标技术堆栈
- AWS Lambda公司
- 亚马逊S3
-
IAM
- AWS安全令牌服务(AWS STS)
目标体系结构
工具
AWS服务
- AWS CLI–AWS命令行界面(AWS CLI)是通过使用命令行shell中的命令与AWS服务交互的统一工具。
- AWS Lambda–AWS Lambda允许您在不配置或管理服务器的情况下运行代码。您只需支付所消耗的计算时间。
- Amazon S3–Amazon Simple Storage Service(Amazon S3)是一种对象存储服务,提供可扩展性、数据可用性、安全性和性能。
- IAM–AWS身份和访问管理(IAM)是一种用于安全控制AWS服务访问的web服务。
- AWS STS-AWS安全令牌服务(AWS STS)使您能够为IAM用户或您认证的用户(联合用户)请求临时、有限的权限凭据。
代码
此模式的源代码作为附件提供,包括以下文件:
- s3UploadSample.jar提供了Lambda函数的源代码,该函数将JSON文档上传到S3存储桶。
- tvm-layer.zip提供了一个可重用的Java库,该库为Lambda函数提供令牌(STS临时凭证),以访问S3存储桶并上载JSON文档。
- token-vending-machine-sample-app.zip提供了用于创建这些工件的源代码和编译说明。
要使用这些文件,请遵循下一节中的说明。
叙事
Determine variable values
| Task | Description | Skills required |
|---|---|---|
| Determine variable values. |
The implementation of this pattern requires includes several variable names that must be used consistently. Determine the values that should be used for each variable, and provide that value when requested in subsequent steps. <AWS Account ID> ─ The 12-digit account ID that is associated with the AWS account you are implementing this pattern in. For information about how to find your AWS cccount ID, see Your AWS account ID and its alias in the IAM documentation. <AWS Region> ─ The AWS Region that you are implementing this pattern in. For more information on AWS Regions, see Regions and Availability Zones on the AWS website. <sample-tenant-name> ─ The name of a tenant to use in the application. We recommend that you use only alphanumeric characters in this value for simplicity, but you can use any valid name for an S3 object key. <sample-tvm-role-name> ─ The name of the IAM role attached to the Lambda function that runs the TVM and sample application. The role name is a string that consists of uppercase and lowercase alphanumeric characters with no spaces. You can also include any of the following characters: underscore (_), plus sign (+), equal sign (=), comma (,), period (.), at sign (@), and hyphen (-). The role name must be unique within the account. <sample-app-role-name> ─ The name of the IAM role that is assumed by the Lambda function when it generates scoped, temporary STS credentials. The role name is a string that consists of uppercase and lowercase alphanumeric characters with no spaces. You can also include any of the following characters: underscore (_), plus sign (+), equal sign (=), comma (,), period (.), at sign (@), and hyphen (-). The role name must be unique within the account. <sample-app-function-name> ─ The name of the Lambda function. This is a string that’s up to 64 characters in length. <sample-app-bucket-name> ─ The name of an S3 bucket that must be accessed with permissions that are scoped to a specific tenant. S3 bucket names:
|
Cloud administrator |
Create an S3 bucket
| Task | Description | Skills required |
|---|---|---|
| Create an S3 bucket for the sample application. |
Use the following AWS CLI command to create an S3 bucket. Provide the <sample-app-bucket-name> value in the code snippet: The Lambda sample application uploads JSON files to this bucket. |
Cloud administrator |
Create the IAM TVM role and policy
| Task | Description | Skills required |
|---|---|---|
| Create a TVM role. |
Use one of the following AWS CLI commands to create an IAM role. Provide the <sample-tvm-role-name> value in the command. For macOS or Linux shells: For the Windows command line: The Lambda sample application assumes this role when the application is invoked. The capability to assume the application role with a scoped policy gives the code broader permissions to access the S3 bucket. |
Cloud administrator |
| Create an inline TVM role policy. |
Use one of the following AWS CLI commands to create an IAM policy. Provide the <sample-tvm-role-name>, <AWS Account ID>, and <sample-app-role-name> values in the command. For macOS or Linux shells: For the Windows command line: This policy is attached to the TVM role. It gives the code the capability to assume the application role, which has broader permissions to access the S3 bucket. |
Cloud administrator |
| Attach the managed Lambda policy. |
Use the following AWS CLI command to attach the This managed policy is attached to the TVM role to permit Lambda to send logs to Amazon CloudWatch. |
Cloud administrator |
Create the IAM application role and policy
| Task | Description | Skills required |
|---|---|---|
| Create the application role. |
Use one of the following AWS CLI commands to create an IAM role. Provide the <sample-app-role-name>, <AWS Account ID>, and <sample-tvm-role-name> values in the command. For macOS or Linux shells: For the Windows command line: The Lambda sample application assumes this role with a scoped policy to get tenant-based access to an S3 bucket. |
Cloud administrator |
| Create an inline application role policy. |
Use one of the following AWS CLI commands to create an IAM policy. Provide the <sample-app-role-name> and <sample-app-bucket-name> values in the command. For macOS or Linux shells: For the Windows command line: This policy is attached to the application role. It provides broad access to objects in the S3 bucket. When the sample application assumes the role, these permissions are scoped to a specific tenant with the TVM's dynamically generated policy. |
Cloud administrator |
Create the Lambda sample application with TVM
| Task | Description | Skills required |
|---|---|---|
| Download the compiled source files. |
Download the |
Cloud administrator |
| Create the Lambda layer. |
Use the following AWS CLI command to create a Lambda layer, which makes the TVM accessible to Lambda. Note: If you aren’t running this command from the location where you downloaded This command creates a Lambda layer that contains the reusable TVM library. |
Cloud administrator, App developer |
| Create the Lambda function. |
Use the following AWS CLI command to create a Lambda function. Provide the <sample-app-function-name>, <AWS Account ID>, <AWS Region>, <sample-tvm-role-name>, <sample-app-bucket-name>, and <sample-app-role-name> values in the command. Note: If you aren’t running this command from the location where you downloaded This command creates a Lambda function with the sample application code and the TVM layer attached. It also sets two environment variables: |
Cloud administrator, App developer |
Test the sample application and TVM
| Task | Description | Skills required |
|---|---|---|
| Invoke the Lambda sample application. |
Use one of the following AWS CLI commands to start the Lambda sample application with its expected payload. Provide the <sample-app-function-name> and <sample-tenant-name> values in the command. For macOS and Linux shells: For the Windows command line: This command calls the Lambda function and returns the result in a Note: Changing the <sample-tenant-name> value in subsequent invocations of this Lambda function alters the location of the JSON document and the permissions the token provides. |
Cloud administrator, App developer |
| View the S3 bucket to see created objects. |
Browse to the S3 bucket ( <sample-app-bucket-name>) that you created earlier. This bucket contains an S3 object prefix with the value of <sample-tenant-name>. Under that prefix, you will find a JSON document named with a UUID. Invoking the sample application multiple times adds more JSON documents. |
Cloud administrator |
| View Cloudwatch logs for the sample application. |
View the Cloudwatch logs associated with the Lambda function named <sample-app-function-name>. For instructions, see Accessing Amazon CloudWatch logs for AWS Lambda in the AWS Lambda documentation. You can view the tenant-scoped policy generated by the TVM in these logs. This tenant-scoped policy gives permissions for the sample application to the Amazon S3 PutObject, GetObject, DeleteObject, and ListBucket APIs, but only for the object prefix associated with <sample-tenant-name>. In subsequent invocations of the sample application, if you change the <sample-tenant-name>, the TVM updates the scoped policy to correspond to the tenant provided in the invocation payload. This dynamically generated policy shows how tenant-scoped access can be maintained with a TVM in SaaS applications. The TVM functionality is provided in a Lambda layer so that it can be attached to other Lambda functions used by an application without having to replicate the code. For an illustration of the dynamically generated policy, see the Additional information section. |
Cloud administrator |
Related resources
-
Isolating Tenants with Dynamically Generated IAM Policies (blog post)
-
Applying Dynamically Generated Isolation Policies in SaaS Environment (blog post)
-
AWS SaaS Boost (an open-source reference environment that helps you move your SaaS offering to AWS)
Additional information
The following Amazon Cloudwatch log shows the dynamically generated policy produced by the TVM code in this pattern. In this screenshot, the <sample-app-bucket-name> is DOC-EXAMPLE-BUCKET and the <sample-tenant-name> is test-tenant-1. The STS credentials returned by this scoped policy are unable to perform any actions on objects in the S3 bucket except for objects that are associated with the object key prefix test-tenant-1.

Attachments
要访问与此文档相关的其他内容,请解压缩以下文件:attachment.zip
- 53 次浏览